ISO/IEC 27002:2013
(Main)Information technology — Security techniques — Code of practice for information security controls
Information technology — Security techniques — Code of practice for information security controls
ISO/IEC 27002:2013 gives guidelines for organizational information security standards and information security management practices including the selection, implementation and management of controls taking into consideration the organization's information security risk environment(s). It is designed to be used by organizations that intend to: select controls within the process of implementing an Information Security Management System based on ISO/IEC 27001; implement commonly accepted information security controls; develop their own information security management guidelines.
Technologies de l'information — Techniques de sécurité — Code de bonne pratique pour le management de la sécurité de l'information
L'ISO 27002:2013 donne des lignes directrices en matière de normes organisationnelles relatives à la sécurité de l'information et des bonnes pratiques de management de la sécurité de l'information, incluant la sélection, la mise en ?uvre et la gestion de mesures de sécurité prenant en compte le ou les environnement(s) de risques de sécurité de l'information de l'organisation. L'ISO 27002:2013 est élaborée à l'intention des organisations désireuses de sélectionner les mesures nécessaires dans le cadre du processus de mise en ?uvre d'un système de management de la sécurité de l'information (SMSI) selon l'ISO/CEI 27001; de mettre en ?uvre des mesures de sécurité de l'information largement reconnues; et d'élaborer leurs propres lignes directrices de management de la sécurité de l'information.
Informacijska tehnologija - Varnostne tehnike - Pravila obnašanja pri kontrolah informacijske varnosti
Ta mednarodni standard podaja smernice za standarde informacijske varnosti organizacij in načine uporabe upravljanja informacijske varnosti, kar vključuje izbiro, izvajanje in upravljanje kontrol, pri čemer upošteva tveganja za informacijsko varnost v okolju organizacije.
Ta mednarodni standard lahko uporabljajo organizacije, ki želijo:
a) izbirati kontrole znotraj procesa izvajanja sistemov upravljanja informacijske varnosti na osnovi standarda ISO/IEC 27001;
b) izvajati splošno sprejete kontrole informacijske varnosti;
c) razvijati lastne smernice za upravljanje informacijske varnosti.
General Information
- Status
- Withdrawn
- Publication Date
- 24-Sep-2013
- Drafting Committee
- ISO/IEC JTC 1/SC 27/WG 1 - Information security management systems
- Current Stage
- 9599 - Withdrawal of International Standard
- Start Date
- 15-Feb-2022
- Completion Date
- 12-Feb-2026
Relations
- Effective Date
- 09-Feb-2026
- Effective Date
- 09-Feb-2026
- Effective Date
- 09-Feb-2026
- Effective Date
- 09-Feb-2026
- Effective Date
- 09-Feb-2026
- Effective Date
- 09-Feb-2026
- Effective Date
- 09-Feb-2026
- Effective Date
- 09-Feb-2026
- Referred By
CEN ISO/TS 19299:2015 - Electronic fee collection - Security framework (ISO/TS 19299:2015) - Effective Date
- 09-Feb-2026
- Effective Date
- 07-Apr-2018
- Effective Date
- 30-May-2009
ISO/IEC 27002:2013 - Information technology -- Security techniques -- Code of practice for information security controls
ISO/IEC 27002:2013 - Information technology -- Security techniques -- Code of practice for information security controls
REDLINE ISO/IEC 27002:2013 - Information technology -- Security techniques -- Code of practice for information security controls
ISO/IEC 27002:2013 - Technologies de l'information -- Techniques de sécurité -- Code de bonne pratique pour le management de la sécurité de l'information
Get Certified
Connect with accredited certification bodies for this standard

BSI Group
BSI (British Standards Institution) is the business standards company that helps organizations make excellence a habit.

Bureau Veritas
Bureau Veritas is a world leader in laboratory testing, inspection and certification services.

DNV
DNV is an independent assurance and risk management provider.
Sponsored listings
Frequently Asked Questions
ISO/IEC 27002:2013 is a standard published by the International Organization for Standardization (ISO). Its full title is "Information technology — Security techniques — Code of practice for information security controls". This standard covers: ISO/IEC 27002:2013 gives guidelines for organizational information security standards and information security management practices including the selection, implementation and management of controls taking into consideration the organization's information security risk environment(s). It is designed to be used by organizations that intend to: select controls within the process of implementing an Information Security Management System based on ISO/IEC 27001; implement commonly accepted information security controls; develop their own information security management guidelines.
ISO/IEC 27002:2013 gives guidelines for organizational information security standards and information security management practices including the selection, implementation and management of controls taking into consideration the organization's information security risk environment(s). It is designed to be used by organizations that intend to: select controls within the process of implementing an Information Security Management System based on ISO/IEC 27001; implement commonly accepted information security controls; develop their own information security management guidelines.
ISO/IEC 27002:2013 is classified under the following ICS (International Classification for Standards) categories: 03.100.70 - Management systems; 35.030 - IT Security; 35.040 - Information coding. The ICS classification helps identify the subject area and facilitates finding related standards.
ISO/IEC 27002:2013 has the following relationships with other standards: It is inter standard links to EN ISO/IEC 29151:2022, EN ISO/IEC 27018:2020, EN ISO/IEC 27011:2020, EN ISO/IEC 29146:2023, EN ISO/IEC 27019:2020, EN ISO/IEC 27017:2021, EN ISO 27799:2016, EN ISO/IEC 27701:2021, CEN ISO/TS 19299:2015, ISO/IEC 27002:2022, ISO/IEC 27002:2005. Understanding these relationships helps ensure you are using the most current and applicable version of the standard.
ISO/IEC 27002:2013 is available in PDF format for immediate download after purchase. The document can be added to your cart and obtained through the secure checkout process. Digital delivery ensures instant access to the complete standard document.
Standards Content (Sample)
SLOVENSKI STANDARD
01-november-2013
Informacijska tehnologija - Varnostne tehnike - Pravila obnašanja pri kontrolah
informacijske varnosti
Information technology -- Security techniques -- Code of practice for information security
controls
Technologies de l'information -- Techniques de sécurité -- Code de bonne pratique pour
le management de la sécurité de l'information
Ta slovenski standard je istoveten z: ISO/IEC 27002:2013
ICS:
35.040 Nabori znakov in kodiranje Character sets and
informacij information coding
2003-01.Slovenski inštitut za standardizacijo. Razmnoževanje celote ali delov tega standarda ni dovoljeno.
INTERNATIONAL ISO/IEC
STANDARD 27002
Second edition
2013-10-01
Information technology — Security
techniques — Code of practice for
information security controls
Technologies de l’information — Techniques de sécurité — Code de
bonne pratique pour le management de la sécurité de l’information
Reference number
©
ISO/IEC 2013
© ISO/IEC 2013
All rights reserved. Unless otherwise specified, no part of this publication may be reproduced or utilized otherwise in any form
or by any means, electronic or mechanical, including photocopying, or posting on the internet or an intranet, without prior
written permission. Permission can be requested from either ISO at the address below or ISO’s member body in the country of
the requester.
ISO copyright office
Case postale 56 • CH-1211 Geneva 20
Tel. + 41 22 749 01 11
Fax + 41 22 749 09 47
E-mail copyright@iso.org
Web www.iso.org
Published in Switzerland
ii © ISO/IEC 2013 – All rights reserved
Contents Page
Foreword .v
0 Introduction .vi
1 Scope . 1
2 Normative references . 1
3 Terms and definitions . 1
4 Structure of this standard . 1
4.1 Clauses . 1
4.2 Control categories . 1
5 Information security policies . 2
5.1 Management direction for information security . 2
6 Organization of information security . 4
6.1 Internal organization . 4
6.2 Mobile devices and teleworking . 6
7 Human resource security . 9
7.1 Prior to employment . 9
7.2 During employment .10
7.3 Termination and change of employment .13
8 Asset management .13
8.1 Responsibility for assets .13
8.2 Information classification .15
8.3 Media handling .17
9 Access control .19
9.1 Business requirements of access control .19
9.2 User access management .21
9.3 User responsibilities .24
9.4 System and application access control .25
10 Cryptography .28
10.1 Cryptographic controls .28
11 Physical and environmental security .30
11.1 Secure areas .30
11.2 Equipment .33
12 Operations security .38
12.1 Operational procedures and responsibilities .38
12.2 Protection from malware .41
12.3 Backup .42
12.4 Logging and monitoring .43
12.5 Control of operational software .45
12.6 Technical vulnerability management .46
12.7 Information systems audit considerations .48
13 Communications security .49
13.1 Network security management .49
13.2 Information transfer .50
14 System acquisition, development and maintenance .54
14.1 Security requirements of information systems .54
14.2 Security in development and support processes .57
14.3 Test data .62
15 Supplier relationships .62
15.1 Information security in supplier relationships .62
© ISO/IEC 2013 – All rights reserved iii
15.2 Supplier service delivery management .66
16 Information security incident management .67
16.1 Management of information security incidents and improvements .67
17 Information security aspects of business continuity management .71
17.1 Information security continuity .71
17.2 Redundancies .73
18 Compliance .74
18.1 Compliance with legal and contractual requirements .74
18.2 Information security reviews .77
Bibliography .79
iv © ISO/IEC 2013 – All rights reserved
Foreword
ISO (the International Organization for Standardization) and IEC (the International Electrotechnical
Commission) form the specialized system for worldwide standardization. National bodies that are
members of ISO or IEC participate in the development of International Standards through technical
committees established by the respective organization to deal with particular fields of technical
activity. ISO and IEC technical committees collaborate in fields of mutual interest. Other international
organizations, governmental and non-governmental, in liaison with ISO and IEC, also take part in the
work. In the field of information technology, ISO and IEC have established a joint technical committee,
ISO/IEC JTC 1.
International Standards are drafted in accordance with the rules given in the ISO/IEC Directives, Part 2.
ISO/IEC 27002 was prepared by Joint Technical Committee ISO/IEC JTC 1, Information technology,
Subcommittee SC 27, IT Security techniques.
Attention is drawn to the possibility that some of the elements of this document may be the subject of
patent rights. ISO shall not be held responsible for identifying any or all such patent rights.
This second edition cancels and replaces the first edition (ISO/IEC 27002:2005), which has been
technically and structurally revised.
© ISO/IEC 2013 – All rights reserved v
0 Introduction
0.1 Background and context
This International Standard is designed for organizations to use as a reference for selecting controls
within the process of implementing an Information Security Management System (ISMS) based on
[10]
ISO/IEC 27001 or as a guidance document for organizations implementing commonly accepted
information security controls. This standard is also intended for use in developing industry- and
organization-specific information security management guidelines, taking into consideration their
specific information security risk environment(s).
Organizations of all types and sizes (including public and private sector, commercial and non-profit)
collect, process, store and transmit information in many forms including electronic, physical and verbal
(e.g. conversations and presentations).
The value of information goes beyond the written words, numbers and images: knowledge, concepts, ideas
and brands are examples of intangible forms of information. In an interconnected world, information and
related processes, systems, networks and personnel involved in their operation, handling and protection
are assets that, like other important business assets, are valuable to an organization’s business and
consequently deserve or require protection against various hazards.
Assets are subject to both deliberate and accidental threats while the related processes, systems,
networks and people have inherent vulnerabilities. Changes to business processes and systems or
other external changes (such as new laws and regulations) may create new information security risks.
Therefore, given the multitude of ways in which threats could take advantage of vulnerabilities to harm
the organization, information security risks are always present. Effective information security reduces
these risks by protecting the organization against threats and vulnerabilities, and then reduces impacts
to its assets.
Information security is achieved by implementing a suitable set of controls, including policies, processes,
procedures, organizational structures and software and hardware functions. These controls need to
be established, implemented, monitored, reviewed and improved, where necessary, to ensure that the
specific security and business objectives of the organization are met. An ISMS such as that specified in
[10]
ISO/IEC 27001 takes a holistic, coordinated view of the organization’s information security risks in
order to implement a comprehensive suite of information security controls under the overall framework
of a coherent management system.
[10]
Many information systems have not been designed to be secure in the sense of ISO/IEC 27001 and this
standard. The security that can be achieved through technical means is limited and should be supported
by appropriate management and procedures. Identifying which controls should be in place requires
careful planning and attention to detail. A successful ISMS requires support by all employees in the
organization. It can also require participation from shareholders, suppliers or other external parties.
Specialist advice from external parties can also be needed.
In a more general sense, effective information security also assures management and other stakeholders
that the organization’s assets are reasonably safe and protected against harm, thereby acting as a
business enabler.
0.2 Information security requirements
It is essential that an organization identifies its security requirements. There are three main sources of
security requirements:
a) the assessment of risks to the organization, taking into account the organization’s overall business
strategy and objectives. Through a risk assessment, threats to assets are identified, vulnerability to
and likelihood of occurrence is evaluated and potential impact is estimated;
b) the legal, statutory, regulatory and contractual requirements that an organization, its trading
partners, contractors and service providers have to satisfy, and their socio-cultural environment;
vi © ISO/IEC 2013 – All rights reserved
c) the set of principles, objectives and business requirements for information handling, processing,
storing, communicating and archiving that an organization has developed to support its operations.
Resources employed in implementing controls need to be balanced against the business harm likely
to result from security issues in the absence of those controls. The results of a risk assessment will
help guide and determine the appropriate management action and priorities for managing information
security risks and for implementing controls selected to protect against these risks.
[11]
ISO/IEC 27005 provides information security risk management guidance, including advice on risk
assessment, risk treatment, risk acceptance, risk communication, risk monitoring and risk review.
0.3 Selecting controls
Controls can be selected from this standard or from other control sets, or new controls can be designed
to meet specific needs as appropriate.
The selection of controls is dependent upon organizational decisions based on the criteria for risk
acceptance, risk treatment options and the general risk management approach applied to the organization,
and should also be subject to all relevant national and international legislation and regulations. Control
selection also depends on the manner in which controls interact to provide defence in depth.
Some of the controls in this standard can be considered as guiding principles for information security
management and applicable for most organizations. The controls are explained in more detail below
along with implementation guidance. More information about selecting controls and other risk treatment
[11]
options can be found in ISO/IEC 27005.
0.4 Developing your own guidelines
This International Standard may be regarded as a starting point for developing organization-specific
guidelines. Not all of the controls and guidance in this code of practice may be applicable. Furthermore,
additional controls and guidelines not included in this standard may be required. When documents are
developed containing additional guidelines or controls, it may be useful to include cross-references to clauses
in this standard where applicable to facilitate compliance checking by auditors and business partners.
0.5 Lifecycle considerations
Information has a natural lifecycle, from creation and origination through storage, processing, use and
transmission to its eventual destruction or decay. The value of, and risks to, assets may vary during their
lifetime (e.g. unauthorized disclosure or theft of a company’s financial accounts is far less significant after
they have been formally published) but information security remains important to some extent at all stages.
Information systems have lifecycles within which they are conceived, specified, designed, developed,
tested, implemented, used, maintained and eventually retired from service and disposed of. Information
security should be taken into account at every stage. New system developments and changes to existing
systems present opportunities for organizations to update and improve security controls, taking actual
incidents and current and projected information security risks into account.
0.6 Related standards
While this standard offers guidance on a broad range of information security controls that are
commonly applied in many different organizations, the remaining standards in the ISO/IEC 27000
family provide complementary advice or requirements on other aspects of the overall process of
managing information security.
Refer to ISO/IEC 27000 for a general introduction to both ISMSs and the family of standards. ISO/IEC 27000
provides a glossary, formally defining most of the terms used throughout the ISO/IEC 27000 family of
standards, and describes the scope and objectives for each member of the family.
© ISO/IEC 2013 – All rights reserved vii
INTERNATIONAL STANDARD ISO/IEC 27002:2013(E)
Information technology — Security techniques — Code of
practice for information security controls
1 Scope
This International Standard gives guidelines for organizational information security standards and
information security management practices including the selection, implementation and management
of controls taking into consideration the organization’s information security risk environment(s).
This International Standard is designed to be used by organizations that intend to:
a) select controls within the process of implementing an Information Security Management System
[10]
based on ISO/IEC 27001;
b) implement commonly accepted information security controls;
c) develop their own information security management guidelines.
2 Normative references
The following documents, in whole or in part, are normatively referenced in this document and are
indispensable for its application. For dated references, only the edition cited applies. For undated
references, the latest edition of the referenced document (including any amendments) applies.
ISO/IEC 27000, Information technology — Security techniques — Information security management
systems — Overview and vocabulary
3 Terms and definitions
For the purposes of this document, the terms and definitions given in ISO/IEC 27000 apply.
4 Structure of this standard
This standard contains 14 security control clauses collectively containing a total of 35 main security
categories and 114 controls.
4.1 Clauses
Each clause defining security controls contains one or more main security categories.
The order of the clauses in this standard does not imply their importance. Depending on the circumstances,
security controls from any or all clauses could be important, therefore each organization applying this
standard should identify applicable controls, how important these are and their application to individual
business processes. Furthermore, lists in this standard are not in priority order.
4.2 Control categories
Each main security control category contains:
a) a control objective stating what is to be achieved;
b) one or more controls that can be applied to achieve the control objective.
© ISO/IEC 2013 – All rights reserved 1
Control descriptions are structured as follows:
Control
Defines the specific control statement, to satisfy the control objective.
Implementation guidance
Provides more detailed information to support the implementation of the control and meeting the
control objective. The guidance may not be entirely suitable or sufficient in all situations and may not
fulfil the organization’s specific control requirements. .
Other information
Provides further information that may need to be considered, for example legal considerations and
references to other standards. If there is no other information to be provided this part is not shown.
5 Information security policies
5.1 Management direction for information security
Objective: To provide management direction and support for information security in accordance with
business requirements and relevant laws and regulations.
5.1.1 Policies for information security
Control
A set of policies for information security should be defined, approved by management, published and
communicated to employees and relevant external parties.
Implementation guidance
At the highest level, organizations should define an “information security policy” which is approved by
management and which sets out the organization’s approach to managing its information security objectives.
Information security policies should address requirements created by:
a) business strategy;
b) regulations, legislation and contracts;
c) the current and projected information security threat environment.
The information security policy should contain statements concerning:
a) definition of information security, objectives and principles to guide all activities relating to
information security;
b) assignment of general and specific responsibilities for information security management to
defined roles;
c) processes for handling deviations and exceptions.
At a lower level, the information security policy should be supported by topic-specific policies, which
further mandate the implementation of information security controls and are typically structured to
address the needs of certain target groups within an organization or to cover certain topics.
Examples of such policy topics include:
a) access control (see Clause 9);
2 © ISO/IEC 2013 – All rights reserved
b) information classification (and handling) (see 8.2);
c) physical and environmental security (see Clause 11);
d) end user oriented topics such as:
1) acceptable use of assets (see 8.1.3);
2) clear desk and clear screen (see 11.2.9);
3) information transfer (see 13.2.1);
4) mobile devices and teleworking (see 6.2);
5) restrictions on software installations and use (see 12.6.2);
e) backup (see 12.3);
f) information transfer (see 13.2);
g) protection from malware (see 12.2);
h) management of technical vulnerabilities (see 12.6.1);
i) cryptographic controls (see Clause 10);
j) communications security (see Clause 13);
k) privacy and protection of personally identifiable information (see 18.1.4);
l) supplier relationships (see Clause 15).
These policies should be communicated to employees and relevant external parties in a form that is
relevant, accessible and understandable to the intended reader, e.g. in the context of an “information
security awareness, education and training programme” (see 7.2.2).
Other information
The need for internal policies for information security varies across organizations. Internal policies
are especially useful in larger and more complex organizations where those defining and approving
the expected levels of control are segregated from those implementing the controls or in situations
where a policy applies to many different people or functions in the organization. Policies for information
security can be issued in a single “information security policy” document or as a set of individual but
related documents.
If any of the information security policies are distributed outside the organization, care should be taken
not to disclose confidential information.
Some organizations use other terms for these policy documents, such as “Standards”, “Directives” or “Rules”.
5.1.2 Review of the policies for information security
Control
The policies for information security should be reviewed at planned intervals or if significant changes
occur to ensure their continuing suitability, adequacy and effectiveness.
Implementation guidance
Each policy should have an owner who has approved management responsibility for the development,
review and evaluation of the policies. The review should include assessing opportunities for improvement
of the organization’s policies and approach to managing information security in response to changes to
the organizational environment, business circumstances, legal conditions or technical environment.
© ISO/IEC 2013 – All rights reserved 3
The review of policies for information security should take the results of management reviews into account.
Management approval for a revised policy should be obtained.
6 Organization of information security
6.1 Internal organization
Objective: To establish a management framework to initiate and control the implementation and
operation of information security within the organization.
6.1.1 Information security roles and responsibilities
Control
All information security responsibilities should be defined and allocated.
Implementation guidance
Allocation of information security responsibilities should be done in accordance with the information
security policies (see 5.1.1). Responsibilities for the protection of individual assets and for carrying out
specific information security processes should be identified. Responsibilities for information security
risk management activities and in particular for acceptance of residual risks should be defined. These
responsibilities should be supplemented, where necessary, with more detailed guidance for specific
sites and information processing facilities. Local responsibilities for the protection of assets and for
carrying out specific security processes should be defined.
Individuals with allocated information security responsibilities may delegate security tasks to others.
Nevertheless they remain accountable and should determine that any delegated tasks have been
correctly performed.
Areas for which individuals are responsible should be stated. In particular the following should take place:
a) the assets and information security processes should be identified and defined;
b) the entity responsible for each asset or information security process should be assigned and the
details of this responsibility should be documented (see 8.1.2);
c) authorization levels should be defined and documented;
d) to be able to fulfil responsibilities in the information security area the appointed individuals should
be competent in the area and be given opportunities to keep up to date with developments;
e) coordination and oversight of information security aspects of supplier relationships should be
identified and documented.
Other information
Many organizations appoint an information security manager to take overall responsibility for the
development and implementation of information security and to support the identification of controls.
However, responsibility for resourcing and implementing the controls will often remain with individual
managers. One common practice is to appoint an owner for each asset who then becomes responsible
for its day-to-day protection.
6.1.2 Segregation of duties
Control
4 © ISO/IEC 2013 – All rights reserved
Conflicting duties and areas of responsibility should be segregated to reduce opportunities for
unauthorized or unintentional modification or misuse of the organization’s assets.
Implementation guidance
Care should be taken that no single person can access, modify or use assets without authorization
or detection. The initiation of an event should be separated from its authorization. The possibility of
collusion should be considered in designing the controls.
Small organizations may find segregation of duties difficult to achieve, but the principle should be
applied as far as is possible and practicable. Whenever it is difficult to segregate, other controls such as
monitoring of activities, audit trails and management supervision should be considered.
Other information
Segregation of duties is a method for reducing the risk of accidental or deliberate misuse of an
organization’s assets.
6.1.3 Contact with authorities
Control
Appropriate contacts with relevant authorities should be maintained.
Implementation guidance
Organizations should have procedures in place that specify when and by whom authorities (e.g. law
enforcement, regulatory bodies, supervisory authorities) should be contacted and how identified
information security incidents should be reported in a timely manner (e.g. if it is suspected that laws
may have been broken).
Other information
Organizations under attack from the Internet may need authorities to take action against the attack source.
Maintaining such contacts may be a requirement to support information security incident management
(see Clause 16) or the business continuity and contingency planning process (see Clause 17). Contacts
with regulatory bodies are also useful to anticipate and prepare for upcoming changes in laws or
regulations, which have to be implemented by the organization. Contacts with other authorities include
utilities, emergency services, electricity suppliers and health and safety, e.g. fire departments (in
connection with business continuity), telecommunication providers (in connection with line routing
and availability) and water suppliers (in connection with cooling facilities for equipment).
6.1.4 Contact with special interest groups
Control
Appropriate contacts with special interest groups or other specialist security forums and professional
associations should be maintained.
Implementation guidance
Membership in special interest groups or forums should be considered as a means to:
a) improve knowledge about best practices and stay up to date with relevant security information;
b) ensure the understanding of the information security environment is current and complete;
c) receive early warnings of alerts, advisories and patches pertaining to attacks and vulnerabilities;
d) gain access to specialist information security advice;
© ISO/IEC 2013 – All rights reserved 5
e) share and exchange information about new technologies, products, threats or vulnerabilities;
f) provide suitable liaison points when dealing with information security incidents (see Clause 16).
Other information
Information sharing agreements can be established to improve cooperation and coordination of security
issues. Such agreements should identify requirements for the protection of confidential information.
6.1.5 Information security in project management
Control
Information security should be addressed in project management, regardless of the type of the project.
Implementation guidance
Information security should be integrated into the organization’s project management method(s) to ensure
that information security risks are identified and addressed as part of a project. This applies generally to
any project regardless of its character, e.g. a project for a core business process, IT, facility management
and other supporting processes. The project management methods in use should require that:
a) information security objectives are included in project objectives;
b) an information security risk assessment is conducted at an early stage of the project to identify
necessary controls;
c) information security is part of all phases of the applied project methodology.
Information security implications should be addressed and reviewed regularly in all projects.
Responsibilities for information security should be defined and allocated to specified roles defined in
the project management methods.
6.2 Mobile devices and teleworking
Objective: To ensure the security of teleworking and use of mobile devices.
6.2.1 Mobile device policy
Control
A policy and supporting security measures should be adopted to manage the risks introduced by using
mobile devices.
Implementation guidance
When using mobile devices, special care should be taken to ensure that business information is not
compromised. The mobile device policy should take into account the risks of working with mobile
devices in unprotected environments.
The mobile device policy should consider:
a) registration of mobile devices;
b) requirements for physical protection;
c) restriction of software installation;
d) requirements for mobile device software versions and for applying patches;
e) restriction of connection to information services;
6 © ISO/IEC 2013 – All rights reserved
f) access controls;
g) cryptographic techniques;
h) malware protection;
i) remote disabling, erasure or lockout;
j) backups;
k) usage of web services and web apps.
Care should be taken when using mobile devices in public places, meeting rooms and other unprotected
areas. Protection should be in place to avoid the unauthorized access to or disclosure of the information
stored and processed by these devices, e.g. using cryptographic techniques (see Clause 10) and enforcing
use of secret authentication information (see 9.2.4).
Mobile devices should also be physically protected against theft especially when left, for example, in cars
and other forms of transport, hotel rooms, conference centres and meeting places. A specific procedure
taking into account legal, insurance and other security requirements of the organization should be
established for cases of theft or loss of mobile devices. Devices carrying important, sensitive or critical
business information should not be left unattended and, where possible, should be physically locked
away, or special locks should be used to secure the devices.
Training should be arranged for personnel using mobile devices to raise their awareness of the additional
risks resulting from this way of working and the controls that should be implemented.
Where the mobile device policy allows the use of privately owned mobile devices, the policy and related
security measures should also consider:
a) separation of private and business use of the devices, including using software to support such
separation and protect business data on a private device;
b) providing access to business information only after users have signed an end user agreement
acknowledging their duties (physical protection, software updating, etc.), waiving ownership of
business data, allowing remote wiping of data by the organization in case of theft or loss of the device
or when no longer authorized to use the service. This policy needs to take account of privacy legislation.
Other information
Mobile device wireless connections are similar to other types of network connection, but have important
differences that should be considered when identifying controls. Typical differences are:
a) some wireless security protocols are immature and have known weaknesses;
b) information stored on mobile devices may not be backed-up because of limited network bandwidth
or because mobile devices may not be connected at the times when backups are scheduled.
Mobile devices generally share common functions, e.g. networking, internet access, e-mail and file
handling, with fixed use devices. Information security controls for the mobile devices generally consist
of those adopted in the fixed use devices and those to address threats raised by their usage outside the
organization’s premises.
6.2.2 Teleworking
Control
A policy and supporting security measures should be implemented to protect information accessed,
processed or stored at teleworking sites.
Implementation guidance
© ISO/IEC 2013 – All rights reserved 7
Organizations allowing teleworking activities should issue a policy that defines the conditions and
restrictions for using teleworking. Where deemed applicable and allowed by law, the following matters
should be considered:
a) the existing physical security of the teleworking site, taking into account the physical security of the
building and the local environment;
b) the proposed physical teleworking environment;
c) the communications security requirements, taking into account the need for remote access to the
organization’s internal systems, the sensitivity of the information that will be accessed and passed
over the communication link and the sensitivity of the internal system;
d) the provision of virtual desktop access that prevents processing and storage of information on
privately owned equipment;
e) the threat of unauthorized access to information or resources from other persons using the
accommodation, e.g. family and friends;
f) the use of home networks and requirements or restrictions on the configuration of wireless
network services;
g) policies and procedures to prevent disputes concerning rights to intellectual property developed on
privately owned equipment;
h) access to privately owned equipment (to verify the security of the machine or during an investigation),
which may be prevented by legislation;
i) software licensing agreements that are such that organizations may become liable for licensing for
client software on workstations owned privately by employees or external party users;
j) malware protection and firewall requirements.
The guidelines and arrangements to be considered should include:
a) the provision of suitable equipment and storage furniture for the teleworking activities, where the
use of privately owned equipment that is not under the control of the organization is not allowed;
b) a definition of the work permitted, the hours of work, the classification of information that may be
held and the internal systems and services that the teleworker is authorized to access;
c) the provision of suitable communication equipment, including methods for securing remote access;
d) physical security;
e) rules and guidance on family and visitor access to equipment and information;
f) the provision of hardware and software support and maintenance;
g) the provision of insurance;
h) the procedures for backup and business continuity;
i) audit and security monitoring;
j) revocation of authority and access rights, and the return of equipment when the teleworking
activities are terminated.
Other information
Teleworking refers to all forms of work outside of the office, including non-traditional work environments,
such as those referred to as “telecommuting”, “flexible workplace”, “remote work” and “virtual work”
environments.
8 © ISO/IEC 2013 – All rights reserved
7 Human resource security
7.1
...
INTERNATIONAL ISO/IEC
STANDARD 27002
Second edition
2013-10-01
Information technology — Security
techniques — Code of practice for
information security controls
Technologies de l’information — Techniques de sécurité — Code de
bonne pratique pour le management de la sécurité de l’information
Reference number
©
ISO/IEC 2013
© ISO/IEC 2013
All rights reserved. Unless otherwise specified, no part of this publication may be reproduced or utilized otherwise in any form
or by any means, electronic or mechanical, including photocopying, or posting on the internet or an intranet, without prior
written permission. Permission can be requested from either ISO at the address below or ISO’s member body in the country of
the requester.
ISO copyright office
Case postale 56 • CH-1211 Geneva 20
Tel. + 41 22 749 01 11
Fax + 41 22 749 09 47
E-mail copyright@iso.org
Web www.iso.org
Published in Switzerland
ii © ISO/IEC 2013 – All rights reserved
Contents Page
Foreword .v
0 Introduction .vi
1 Scope . 1
2 Normative references . 1
3 Terms and definitions . 1
4 Structure of this standard . 1
4.1 Clauses . 1
4.2 Control categories . 1
5 Information security policies . 2
5.1 Management direction for information security . 2
6 Organization of information security . 4
6.1 Internal organization . 4
6.2 Mobile devices and teleworking . 6
7 Human resource security . 9
7.1 Prior to employment . 9
7.2 During employment .10
7.3 Termination and change of employment .13
8 Asset management .13
8.1 Responsibility for assets .13
8.2 Information classification .15
8.3 Media handling .17
9 Access control .19
9.1 Business requirements of access control .19
9.2 User access management .21
9.3 User responsibilities .24
9.4 System and application access control .25
10 Cryptography .28
10.1 Cryptographic controls .28
11 Physical and environmental security .30
11.1 Secure areas .30
11.2 Equipment .33
12 Operations security .38
12.1 Operational procedures and responsibilities .38
12.2 Protection from malware .41
12.3 Backup .42
12.4 Logging and monitoring .43
12.5 Control of operational software .45
12.6 Technical vulnerability management .46
12.7 Information systems audit considerations .48
13 Communications security .49
13.1 Network security management .49
13.2 Information transfer .50
14 System acquisition, development and maintenance .54
14.1 Security requirements of information systems .54
14.2 Security in development and support processes .57
14.3 Test data .62
15 Supplier relationships .62
15.1 Information security in supplier relationships .62
© ISO/IEC 2013 – All rights reserved iii
15.2 Supplier service delivery management .66
16 Information security incident management .67
16.1 Management of information security incidents and improvements .67
17 Information security aspects of business continuity management .71
17.1 Information security continuity .71
17.2 Redundancies .73
18 Compliance .74
18.1 Compliance with legal and contractual requirements .74
18.2 Information security reviews .77
Bibliography .79
iv © ISO/IEC 2013 – All rights reserved
Foreword
ISO (the International Organization for Standardization) and IEC (the International Electrotechnical
Commission) form the specialized system for worldwide standardization. National bodies that are
members of ISO or IEC participate in the development of International Standards through technical
committees established by the respective organization to deal with particular fields of technical
activity. ISO and IEC technical committees collaborate in fields of mutual interest. Other international
organizations, governmental and non-governmental, in liaison with ISO and IEC, also take part in the
work. In the field of information technology, ISO and IEC have established a joint technical committee,
ISO/IEC JTC 1.
International Standards are drafted in accordance with the rules given in the ISO/IEC Directives, Part 2.
ISO/IEC 27002 was prepared by Joint Technical Committee ISO/IEC JTC 1, Information technology,
Subcommittee SC 27, IT Security techniques.
Attention is drawn to the possibility that some of the elements of this document may be the subject of
patent rights. ISO shall not be held responsible for identifying any or all such patent rights.
This second edition cancels and replaces the first edition (ISO/IEC 27002:2005), which has been
technically and structurally revised.
© ISO/IEC 2013 – All rights reserved v
0 Introduction
0.1 Background and context
This International Standard is designed for organizations to use as a reference for selecting controls
within the process of implementing an Information Security Management System (ISMS) based on
[10]
ISO/IEC 27001 or as a guidance document for organizations implementing commonly accepted
information security controls. This standard is also intended for use in developing industry- and
organization-specific information security management guidelines, taking into consideration their
specific information security risk environment(s).
Organizations of all types and sizes (including public and private sector, commercial and non-profit)
collect, process, store and transmit information in many forms including electronic, physical and verbal
(e.g. conversations and presentations).
The value of information goes beyond the written words, numbers and images: knowledge, concepts, ideas
and brands are examples of intangible forms of information. In an interconnected world, information and
related processes, systems, networks and personnel involved in their operation, handling and protection
are assets that, like other important business assets, are valuable to an organization’s business and
consequently deserve or require protection against various hazards.
Assets are subject to both deliberate and accidental threats while the related processes, systems,
networks and people have inherent vulnerabilities. Changes to business processes and systems or
other external changes (such as new laws and regulations) may create new information security risks.
Therefore, given the multitude of ways in which threats could take advantage of vulnerabilities to harm
the organization, information security risks are always present. Effective information security reduces
these risks by protecting the organization against threats and vulnerabilities, and then reduces impacts
to its assets.
Information security is achieved by implementing a suitable set of controls, including policies, processes,
procedures, organizational structures and software and hardware functions. These controls need to
be established, implemented, monitored, reviewed and improved, where necessary, to ensure that the
specific security and business objectives of the organization are met. An ISMS such as that specified in
[10]
ISO/IEC 27001 takes a holistic, coordinated view of the organization’s information security risks in
order to implement a comprehensive suite of information security controls under the overall framework
of a coherent management system.
[10]
Many information systems have not been designed to be secure in the sense of ISO/IEC 27001 and this
standard. The security that can be achieved through technical means is limited and should be supported
by appropriate management and procedures. Identifying which controls should be in place requires
careful planning and attention to detail. A successful ISMS requires support by all employees in the
organization. It can also require participation from shareholders, suppliers or other external parties.
Specialist advice from external parties can also be needed.
In a more general sense, effective information security also assures management and other stakeholders
that the organization’s assets are reasonably safe and protected against harm, thereby acting as a
business enabler.
0.2 Information security requirements
It is essential that an organization identifies its security requirements. There are three main sources of
security requirements:
a) the assessment of risks to the organization, taking into account the organization’s overall business
strategy and objectives. Through a risk assessment, threats to assets are identified, vulnerability to
and likelihood of occurrence is evaluated and potential impact is estimated;
b) the legal, statutory, regulatory and contractual requirements that an organization, its trading
partners, contractors and service providers have to satisfy, and their socio-cultural environment;
vi © ISO/IEC 2013 – All rights reserved
c) the set of principles, objectives and business requirements for information handling, processing,
storing, communicating and archiving that an organization has developed to support its operations.
Resources employed in implementing controls need to be balanced against the business harm likely
to result from security issues in the absence of those controls. The results of a risk assessment will
help guide and determine the appropriate management action and priorities for managing information
security risks and for implementing controls selected to protect against these risks.
[11]
ISO/IEC 27005 provides information security risk management guidance, including advice on risk
assessment, risk treatment, risk acceptance, risk communication, risk monitoring and risk review.
0.3 Selecting controls
Controls can be selected from this standard or from other control sets, or new controls can be designed
to meet specific needs as appropriate.
The selection of controls is dependent upon organizational decisions based on the criteria for risk
acceptance, risk treatment options and the general risk management approach applied to the organization,
and should also be subject to all relevant national and international legislation and regulations. Control
selection also depends on the manner in which controls interact to provide defence in depth.
Some of the controls in this standard can be considered as guiding principles for information security
management and applicable for most organizations. The controls are explained in more detail below
along with implementation guidance. More information about selecting controls and other risk treatment
[11]
options can be found in ISO/IEC 27005.
0.4 Developing your own guidelines
This International Standard may be regarded as a starting point for developing organization-specific
guidelines. Not all of the controls and guidance in this code of practice may be applicable. Furthermore,
additional controls and guidelines not included in this standard may be required. When documents are
developed containing additional guidelines or controls, it may be useful to include cross-references to clauses
in this standard where applicable to facilitate compliance checking by auditors and business partners.
0.5 Lifecycle considerations
Information has a natural lifecycle, from creation and origination through storage, processing, use and
transmission to its eventual destruction or decay. The value of, and risks to, assets may vary during their
lifetime (e.g. unauthorized disclosure or theft of a company’s financial accounts is far less significant after
they have been formally published) but information security remains important to some extent at all stages.
Information systems have lifecycles within which they are conceived, specified, designed, developed,
tested, implemented, used, maintained and eventually retired from service and disposed of. Information
security should be taken into account at every stage. New system developments and changes to existing
systems present opportunities for organizations to update and improve security controls, taking actual
incidents and current and projected information security risks into account.
0.6 Related standards
While this standard offers guidance on a broad range of information security controls that are
commonly applied in many different organizations, the remaining standards in the ISO/IEC 27000
family provide complementary advice or requirements on other aspects of the overall process of
managing information security.
Refer to ISO/IEC 27000 for a general introduction to both ISMSs and the family of standards. ISO/IEC 27000
provides a glossary, formally defining most of the terms used throughout the ISO/IEC 27000 family of
standards, and describes the scope and objectives for each member of the family.
© ISO/IEC 2013 – All rights reserved vii
INTERNATIONAL STANDARD ISO/IEC 27002:2013(E)
Information technology — Security techniques — Code of
practice for information security controls
1 Scope
This International Standard gives guidelines for organizational information security standards and
information security management practices including the selection, implementation and management
of controls taking into consideration the organization’s information security risk environment(s).
This International Standard is designed to be used by organizations that intend to:
a) select controls within the process of implementing an Information Security Management System
[10]
based on ISO/IEC 27001;
b) implement commonly accepted information security controls;
c) develop their own information security management guidelines.
2 Normative references
The following documents, in whole or in part, are normatively referenced in this document and are
indispensable for its application. For dated references, only the edition cited applies. For undated
references, the latest edition of the referenced document (including any amendments) applies.
ISO/IEC 27000, Information technology — Security techniques — Information security management
systems — Overview and vocabulary
3 Terms and definitions
For the purposes of this document, the terms and definitions given in ISO/IEC 27000 apply.
4 Structure of this standard
This standard contains 14 security control clauses collectively containing a total of 35 main security
categories and 114 controls.
4.1 Clauses
Each clause defining security controls contains one or more main security categories.
The order of the clauses in this standard does not imply their importance. Depending on the circumstances,
security controls from any or all clauses could be important, therefore each organization applying this
standard should identify applicable controls, how important these are and their application to individual
business processes. Furthermore, lists in this standard are not in priority order.
4.2 Control categories
Each main security control category contains:
a) a control objective stating what is to be achieved;
b) one or more controls that can be applied to achieve the control objective.
© ISO/IEC 2013 – All rights reserved 1
Control descriptions are structured as follows:
Control
Defines the specific control statement, to satisfy the control objective.
Implementation guidance
Provides more detailed information to support the implementation of the control and meeting the
control objective. The guidance may not be entirely suitable or sufficient in all situations and may not
fulfil the organization’s specific control requirements. .
Other information
Provides further information that may need to be considered, for example legal considerations and
references to other standards. If there is no other information to be provided this part is not shown.
5 Information security policies
5.1 Management direction for information security
Objective: To provide management direction and support for information security in accordance with
business requirements and relevant laws and regulations.
5.1.1 Policies for information security
Control
A set of policies for information security should be defined, approved by management, published and
communicated to employees and relevant external parties.
Implementation guidance
At the highest level, organizations should define an “information security policy” which is approved by
management and which sets out the organization’s approach to managing its information security objectives.
Information security policies should address requirements created by:
a) business strategy;
b) regulations, legislation and contracts;
c) the current and projected information security threat environment.
The information security policy should contain statements concerning:
a) definition of information security, objectives and principles to guide all activities relating to
information security;
b) assignment of general and specific responsibilities for information security management to
defined roles;
c) processes for handling deviations and exceptions.
At a lower level, the information security policy should be supported by topic-specific policies, which
further mandate the implementation of information security controls and are typically structured to
address the needs of certain target groups within an organization or to cover certain topics.
Examples of such policy topics include:
a) access control (see Clause 9);
2 © ISO/IEC 2013 – All rights reserved
b) information classification (and handling) (see 8.2);
c) physical and environmental security (see Clause 11);
d) end user oriented topics such as:
1) acceptable use of assets (see 8.1.3);
2) clear desk and clear screen (see 11.2.9);
3) information transfer (see 13.2.1);
4) mobile devices and teleworking (see 6.2);
5) restrictions on software installations and use (see 12.6.2);
e) backup (see 12.3);
f) information transfer (see 13.2);
g) protection from malware (see 12.2);
h) management of technical vulnerabilities (see 12.6.1);
i) cryptographic controls (see Clause 10);
j) communications security (see Clause 13);
k) privacy and protection of personally identifiable information (see 18.1.4);
l) supplier relationships (see Clause 15).
These policies should be communicated to employees and relevant external parties in a form that is
relevant, accessible and understandable to the intended reader, e.g. in the context of an “information
security awareness, education and training programme” (see 7.2.2).
Other information
The need for internal policies for information security varies across organizations. Internal policies
are especially useful in larger and more complex organizations where those defining and approving
the expected levels of control are segregated from those implementing the controls or in situations
where a policy applies to many different people or functions in the organization. Policies for information
security can be issued in a single “information security policy” document or as a set of individual but
related documents.
If any of the information security policies are distributed outside the organization, care should be taken
not to disclose confidential information.
Some organizations use other terms for these policy documents, such as “Standards”, “Directives” or “Rules”.
5.1.2 Review of the policies for information security
Control
The policies for information security should be reviewed at planned intervals or if significant changes
occur to ensure their continuing suitability, adequacy and effectiveness.
Implementation guidance
Each policy should have an owner who has approved management responsibility for the development,
review and evaluation of the policies. The review should include assessing opportunities for improvement
of the organization’s policies and approach to managing information security in response to changes to
the organizational environment, business circumstances, legal conditions or technical environment.
© ISO/IEC 2013 – All rights reserved 3
The review of policies for information security should take the results of management reviews into account.
Management approval for a revised policy should be obtained.
6 Organization of information security
6.1 Internal organization
Objective: To establish a management framework to initiate and control the implementation and
operation of information security within the organization.
6.1.1 Information security roles and responsibilities
Control
All information security responsibilities should be defined and allocated.
Implementation guidance
Allocation of information security responsibilities should be done in accordance with the information
security policies (see 5.1.1). Responsibilities for the protection of individual assets and for carrying out
specific information security processes should be identified. Responsibilities for information security
risk management activities and in particular for acceptance of residual risks should be defined. These
responsibilities should be supplemented, where necessary, with more detailed guidance for specific
sites and information processing facilities. Local responsibilities for the protection of assets and for
carrying out specific security processes should be defined.
Individuals with allocated information security responsibilities may delegate security tasks to others.
Nevertheless they remain accountable and should determine that any delegated tasks have been
correctly performed.
Areas for which individuals are responsible should be stated. In particular the following should take place:
a) the assets and information security processes should be identified and defined;
b) the entity responsible for each asset or information security process should be assigned and the
details of this responsibility should be documented (see 8.1.2);
c) authorization levels should be defined and documented;
d) to be able to fulfil responsibilities in the information security area the appointed individuals should
be competent in the area and be given opportunities to keep up to date with developments;
e) coordination and oversight of information security aspects of supplier relationships should be
identified and documented.
Other information
Many organizations appoint an information security manager to take overall responsibility for the
development and implementation of information security and to support the identification of controls.
However, responsibility for resourcing and implementing the controls will often remain with individual
managers. One common practice is to appoint an owner for each asset who then becomes responsible
for its day-to-day protection.
6.1.2 Segregation of duties
Control
4 © ISO/IEC 2013 – All rights reserved
Conflicting duties and areas of responsibility should be segregated to reduce opportunities for
unauthorized or unintentional modification or misuse of the organization’s assets.
Implementation guidance
Care should be taken that no single person can access, modify or use assets without authorization
or detection. The initiation of an event should be separated from its authorization. The possibility of
collusion should be considered in designing the controls.
Small organizations may find segregation of duties difficult to achieve, but the principle should be
applied as far as is possible and practicable. Whenever it is difficult to segregate, other controls such as
monitoring of activities, audit trails and management supervision should be considered.
Other information
Segregation of duties is a method for reducing the risk of accidental or deliberate misuse of an
organization’s assets.
6.1.3 Contact with authorities
Control
Appropriate contacts with relevant authorities should be maintained.
Implementation guidance
Organizations should have procedures in place that specify when and by whom authorities (e.g. law
enforcement, regulatory bodies, supervisory authorities) should be contacted and how identified
information security incidents should be reported in a timely manner (e.g. if it is suspected that laws
may have been broken).
Other information
Organizations under attack from the Internet may need authorities to take action against the attack source.
Maintaining such contacts may be a requirement to support information security incident management
(see Clause 16) or the business continuity and contingency planning process (see Clause 17). Contacts
with regulatory bodies are also useful to anticipate and prepare for upcoming changes in laws or
regulations, which have to be implemented by the organization. Contacts with other authorities include
utilities, emergency services, electricity suppliers and health and safety, e.g. fire departments (in
connection with business continuity), telecommunication providers (in connection with line routing
and availability) and water suppliers (in connection with cooling facilities for equipment).
6.1.4 Contact with special interest groups
Control
Appropriate contacts with special interest groups or other specialist security forums and professional
associations should be maintained.
Implementation guidance
Membership in special interest groups or forums should be considered as a means to:
a) improve knowledge about best practices and stay up to date with relevant security information;
b) ensure the understanding of the information security environment is current and complete;
c) receive early warnings of alerts, advisories and patches pertaining to attacks and vulnerabilities;
d) gain access to specialist information security advice;
© ISO/IEC 2013 – All rights reserved 5
e) share and exchange information about new technologies, products, threats or vulnerabilities;
f) provide suitable liaison points when dealing with information security incidents (see Clause 16).
Other information
Information sharing agreements can be established to improve cooperation and coordination of security
issues. Such agreements should identify requirements for the protection of confidential information.
6.1.5 Information security in project management
Control
Information security should be addressed in project management, regardless of the type of the project.
Implementation guidance
Information security should be integrated into the organization’s project management method(s) to ensure
that information security risks are identified and addressed as part of a project. This applies generally to
any project regardless of its character, e.g. a project for a core business process, IT, facility management
and other supporting processes. The project management methods in use should require that:
a) information security objectives are included in project objectives;
b) an information security risk assessment is conducted at an early stage of the project to identify
necessary controls;
c) information security is part of all phases of the applied project methodology.
Information security implications should be addressed and reviewed regularly in all projects.
Responsibilities for information security should be defined and allocated to specified roles defined in
the project management methods.
6.2 Mobile devices and teleworking
Objective: To ensure the security of teleworking and use of mobile devices.
6.2.1 Mobile device policy
Control
A policy and supporting security measures should be adopted to manage the risks introduced by using
mobile devices.
Implementation guidance
When using mobile devices, special care should be taken to ensure that business information is not
compromised. The mobile device policy should take into account the risks of working with mobile
devices in unprotected environments.
The mobile device policy should consider:
a) registration of mobile devices;
b) requirements for physical protection;
c) restriction of software installation;
d) requirements for mobile device software versions and for applying patches;
e) restriction of connection to information services;
6 © ISO/IEC 2013 – All rights reserved
f) access controls;
g) cryptographic techniques;
h) malware protection;
i) remote disabling, erasure or lockout;
j) backups;
k) usage of web services and web apps.
Care should be taken when using mobile devices in public places, meeting rooms and other unprotected
areas. Protection should be in place to avoid the unauthorized access to or disclosure of the information
stored and processed by these devices, e.g. using cryptographic techniques (see Clause 10) and enforcing
use of secret authentication information (see 9.2.4).
Mobile devices should also be physically protected against theft especially when left, for example, in cars
and other forms of transport, hotel rooms, conference centres and meeting places. A specific procedure
taking into account legal, insurance and other security requirements of the organization should be
established for cases of theft or loss of mobile devices. Devices carrying important, sensitive or critical
business information should not be left unattended and, where possible, should be physically locked
away, or special locks should be used to secure the devices.
Training should be arranged for personnel using mobile devices to raise their awareness of the additional
risks resulting from this way of working and the controls that should be implemented.
Where the mobile device policy allows the use of privately owned mobile devices, the policy and related
security measures should also consider:
a) separation of private and business use of the devices, including using software to support such
separation and protect business data on a private device;
b) providing access to business information only after users have signed an end user agreement
acknowledging their duties (physical protection, software updating, etc.), waiving ownership of
business data, allowing remote wiping of data by the organization in case of theft or loss of the device
or when no longer authorized to use the service. This policy needs to take account of privacy legislation.
Other information
Mobile device wireless connections are similar to other types of network connection, but have important
differences that should be considered when identifying controls. Typical differences are:
a) some wireless security protocols are immature and have known weaknesses;
b) information stored on mobile devices may not be backed-up because of limited network bandwidth
or because mobile devices may not be connected at the times when backups are scheduled.
Mobile devices generally share common functions, e.g. networking, internet access, e-mail and file
handling, with fixed use devices. Information security controls for the mobile devices generally consist
of those adopted in the fixed use devices and those to address threats raised by their usage outside the
organization’s premises.
6.2.2 Teleworking
Control
A policy and supporting security measures should be implemented to protect information accessed,
processed or stored at teleworking sites.
Implementation guidance
© ISO/IEC 2013 – All rights reserved 7
Organizations allowing teleworking activities should issue a policy that defines the conditions and
restrictions for using teleworking. Where deemed applicable and allowed by law, the following matters
should be considered:
a) the existing physical security of the teleworking site, taking into account the physical security of the
building and the local environment;
b) the proposed physical teleworking environment;
c) the communications security requirements, taking into account the need for remote access to the
organization’s internal systems, the sensitivity of the information that will be accessed and passed
over the communication link and the sensitivity of the internal system;
d) the provision of virtual desktop access that prevents processing and storage of information on
privately owned equipment;
e) the threat of unauthorized access to information or resources from other persons using the
accommodation, e.g. family and friends;
f) the use of home networks and requirements or restrictions on the configuration of wireless
network services;
g) policies and procedures to prevent disputes concerning rights to intellectual property developed on
privately owned equipment;
h) access to privately owned equipment (to verify the security of the machine or during an investigation),
which may be prevented by legislation;
i) software licensing agreements that are such that organizations may become liable for licensing for
client software on workstations owned privately by employees or external party users;
j) malware protection and firewall requirements.
The guidelines and arrangements to be considered should include:
a) the provision of suitable equipment and storage furniture for the teleworking activities, where the
use of privately owned equipment that is not under the control of the organization is not allowed;
b) a definition of the work permitted, the hours of work, the classification of information that may be
held and the internal systems and services that the teleworker is authorized to access;
c) the provision of suitable communication equipment, including methods for securing remote access;
d) physical security;
e) rules and guidance on family and visitor access to equipment and information;
f) the provision of hardware and software support and maintenance;
g) the provision of insurance;
h) the procedures for backup and business continuity;
i) audit and security monitoring;
j) revocation of authority and access rights, and the return of equipment when the teleworking
activities are terminated.
Other information
Teleworking refers to all forms of work outside of the office, including non-traditional work environments,
such as those referred to as “telecommuting”, “flexible workplace”, “remote work” and “virtual work”
environments.
8 © ISO/IEC 2013 – All rights reserved
7 Human resource security
7.1 Prior to employment
Objective: To ensure that employees and contractors understand their responsibilities and are suit-
able for the roles for which they are considered.
7.1.1 Screening
Control
Background verification checks on all candidates for employment should be carried out in accordance
with relevant laws, regulations and ethics and should be proportional to the business requirements, the
classification of the information to be accessed and the perceived risks.
Implementation guidance
Verification should take into account all relevant privacy, protection of personally identifiable
information and employment based legislation, and should, where permitted, include the following:
a) availability of satisfactory character references, e.g. one business and one personal;
b) a verification (for completeness and accuracy) of the applicant’s curriculum vitae;
c) confirmation of claimed academic and professional qualifications;
d) independent identity verification (passport or similar document);
e) more detailed verification, such as credit review or review of criminal records.
When an individual is hired for a specific information security role, organizations should make sure
the candidate:
a) has the necessary competence to perform the security role;
b) can be trusted to take on the role, especially if the r
...
ISO/IEC
Information
technology
Security techniques
Code of practice
for information
security controls
Second edition
2013-10-01
Our vision Our process
To be the world’s leading provider of high qual- Our standards are developed by experts
ity, globally relevant International Standards all over the world who work on a volunteer
through its members and stakeholders. or part-time basis. We sell International
Standards to recover the costs of organizing
this process and making standards widely
Our mission
available.
ISO develops high quality voluntary
Please respect our licensing terms and
International Standards that facilitate interna-
copyright to ensure this system remains
tional exchange of goods and services, support
independent.
sustainable and equitable economic growth,
If you would like to contribute to the devel-
promote innovation and protect health, safety
opment of ISO standards, please contact the
and the environment.
ISO Member Body in your country:
www.iso.org/iso/home/about/iso_mem-
bers.htm
This document has been prepared by:
ISO/IEC JTC 1, Information technology, SC 27,
IT Security techniques. All rights reserved. Unless otherwise speci-
fied, no part of this publication may be repro-
Committee members:
duced or utilized otherwise in any form or
ABNT, AENOR, AFNOR, ANSI, ASI, ASRO, BIS,
by any means, electronic or mechanical,
BSI, BSJ, CODINORM, CYS, DGN, DIN, DS, DSM,
including photocopy, or posting on the inter-
DTR, ESMA, EVS, GOST R, IANOR, ILNAS,
net or intranet, without prior permission.
IMANOR, INDECOPI, INN, IRAM, ISRM, JISC,
Permission can be requested from either ISO
KATS, KAZMEMST, KEBS, MSB, NBN, NEN,
at the address below or ISO’s member body
NSAI, PKN, SA, SABS, SAC, SCC, SFS, SII, SIS,
in the country of the requester:
SIST, SLSI, SN, SNV, SNZ, SPRING SG, SUTN,
© ISO/IEC 2013, Published in Switzerland
TISI, UNI, UNIT, UNMZ, (ISC)2, CCETT, Cloud
security alliance, ECBS, Ecma International,
ISO copyright office
ENISA, EPC, ISACA, ISSEA, ITU, Mastercard,
Case postale 56 • CH-1211 Geneva 20
Mastercard - Europe.
Tel. +41 22 749 01 11
Fax. +41 22 749 09 47
This list reflects contributing members at the
E-mail copyright@iso.org
time of publication.
Web www.iso.org
Cover photo credit: ISO/CS, 2013
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
Executive summary
• Organizations of all types and sizes col- It brings these controls together as a
lect, process, store and transmit infor- code of practice based on the controls
mation in many forms. This information that are commonly applied in many dif-
is valuable to an organization’s business ferent organizations.
and operations. • Effective information security also
• In today’s interconnected and mobile assures management and other stake-
world, information is processed us- holders that the organization’s assets
ing systems and networks that employ are safe, thereby acting as a business
state-of-the-art technology. It is vital to enabler.
protect this information against both • Other International Standards in the
deliberate and accidental threats and ISO/IEC 27000 family give complemen-
vulnerabilities. tary advice or requirements on other
• ISO/IEC 27002 helps organizations to aspects of the overall process of manag-
keep secure both their information as- ing information security.
sets and those of their customers.
• It offers organizations a wide selection
of security controls, together with ac-
companying implementation guidance.
© ISO/IEC 2013 – All rights reserved
Contents Page
Our vision .2
Our mission .2
Our process .2
Executive summary .3
Foreword .6
0 Introduction .7
1 Scope .10
2 Normative references .10
3 Terms and definitions .10
4 Structure of this standard .10
4.1 Clauses .10
4.2 Control categories .10
5 Information security policies .11
5.1 Management direction for information security .11
6 Organization of information security .12
6.1 Internal organization .12
6.2 Mobile devices and teleworking .14
7 Human resource security .17
7.1 Prior to employment .17
7.2 During employment .18
7.3 Termination and change of employment .20
8 Asset management .21
8.1 Responsibility for assets .21
8.2 Information classification .23
8.3 Media handling .24
9 Access control .26
9.1 Business requirements of access control .26
9.2 User access management .28
9.3 User responsibilities .31
9.4 System and application access control .32
10 Cryptography .35
10.1 Cryptographic controls .35
11 Physical and environmental security .37
11.1 Secure areas .37
11.2 Equipment .40
12 Operations security .44
12.1 Operational procedures and responsibilities .44
12.2 Protection from malware .47
12.3 Backup .48
12.4 Logging and monitoring .49
12.5 Control of operational software .50
12.6 Technical vulnerability management .51
© ISO/IEC 2013 – All rights reserved
12.7 Information systems audit considerations .53
13 Communications security .54
13.1 Network security management .54
13.2 Information transfer .55
14 System acquisition, development and maintenance .58
14.1 Security requirements of information systems .58
14.2 Security in development and support processes .61
14.3 Test data .66
15 Supplier relationships .66
15.1 Information security in supplier relationships .66
15.2 Supplier service delivery management .70
16 Information security incident management .71
16.1 Management of information security incidents and improvements .71
17 Information security aspects of business continuity management .75
17.1 Information security continuity .75
17.2 Redundancies .77
18 Compliance .77
18.1 Compliance with legal and contractual requirements .77
18.2 Information security reviews .80
Bibliography .82
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
Foreword
ISO (the International Organization for International Standards are drafted in accord-
Standardization) and IEC (the International ance with the rules given in the ISO/IEC
Electrotechnical Commission) form the special- Directives, Part 2.
ized system for worldwide standardization.
ISO/IEC 27002 was prepared by Joint Technical
National bodies that are members of ISO or IEC
Committee ISO/IEC JTC 1, Information technol-
participate in the development of International
ogy, Subcommittee SC 27, IT Security techniques.
Standards through technical committees estab-
lished by the respective organization to deal
Attention is drawn to the possibility that some
with particular fields of technical activity. ISO
of the elements of this document may be the
and IEC technical committees collaborate in
subject of patent rights. ISO shall not be held
fields of mutual interest. Other international
responsible for identifying any or all such pat-
organizations, governmental and non-govern-
ent rights.
mental, in liaison with ISO and IEC, also take
part in the work. In the field of information
This second edition cancels and replaces the
technology, ISO and IEC have established a joint
first edition (ISO/IEC 27002:2005), which has
technical committee, ISO/IEC JTC 1.
been technically and structurally revised.
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
0 Introduction
0.1 Background and context Information security is achieved by implement-
ing a suitable set of controls, including policies,
This International Standard is designed for
processes, procedures, organizational struc-
organizations to use as a reference for selecting
tures and software and hardware functions.
controls within the process of implementing
These controls need to be established, imple-
an Information Security Management System
mented, monitored, reviewed and improved,
[10]
(ISMS) based on ISO/IEC 27001 or as a guid-
where necessary, to ensure that the specific
ance document for organizations implementing
security and business objectives of the organiza-
commonly accepted information security con-
tion are met. An ISMS such as that specified in
trols. This standard is also intended for use in
[10]
ISO/IEC 27001 takes a holistic, coordinated
developing industry- and organization-specific
view of the organization’s information security
information security management guidelines,
risks in order to implement a comprehensive
taking into consideration their specific infor-
suite of information security controls under
mation security risk environment(s).
the overall framework of a coherent manage-
ment system.
Organizations of all types and sizes (includ-
ing public and private sector, commercial and
Many information systems have not been
non-profit) collect, process, store and transmit
designed to be secure in the sense of
information in many forms including electronic,
[10]
ISO/IEC 27001 and this standard. The secu-
physical and verbal (e.g. conversations and
rity that can be achieved through technical
presentations).
means is limited and should be supported
by appropriate management and procedures.
The value of information goes beyond the writ-
Identifying which controls should be in place
ten words, numbers and images: knowledge,
requires careful planning and attention to
concepts, ideas and brands are examples of
detail. A successful ISMS requires support by
intangible forms of information. In an inter-
all employees in the organization. It can also
connected world, information and related
require participation from shareholders, suppli-
processes, systems, networks and personnel
ers or other external parties. Specialist advice
involved in their operation, handling and pro-
from external parties can also be needed.
tection are assets that, like other important
business assets, are valuable to an organiza-
In a more general sense, effective information
tion’s business and consequently deserve or
security also assures management and other
require protection against various hazards.
stakeholders that the organization’s assets are
reasonably safe and protected against harm,
Assets are subject to both deliberate and acci-
thereby acting as a business enabler.
dental threats while the related processes,
systems, networks and people have inherent
0.2 Information security requirements
vulnerabilities. Changes to business processes
and systems or other external changes (such It is essential that an organization identifies its
as new laws and regulations) may create new security requirements. There are three main
information security risks. Therefore, given sources of security requirements:
the multitude of ways in which threats could
a) the assessment of risks to the organiza-
take advantage of vulnerabilities to harm the
tion, taking into account the organiza-
organization, information security risks are
tion’s overall business strategy and
always present. Effective information security
objectives. Through a risk assessment,
reduces these risks by protecting the organi-
threats to assets are identified, vulner-
zation against threats and vulnerabilities, and
ability to and likelihood of occurrence
then reduces impacts to its assets.
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
is evaluated and potential impact is guidance. More information about selecting
estimated; controls and other risk treatment options can
[11]
be found in ISO/IEC 27005.
b) the legal, statutory, regulatory and con-
tractual requirements that an organiza-
0.4 Developing your own guidelines
tion, its trading partners, contractors
This International Standard may be regarded
and service providers have to satisfy,
as a starting point for developing organization-
and their socio-cultural environment;
specific guidelines. Not all of the controls and
c) the set of principles, objectives and busi-
guidance in this code of practice may be appli-
ness requirements for information han-
cable. Furthermore, additional controls and
dling, processing, storing, communicat-
guidelines not included in this standard may
ing and archiving that an organization
be required. When documents are developed
has developed to support its operations.
containing additional guidelines or controls,
it may be useful to include cross-references
Resources employed in implementing controls
to clauses in this standard where applicable
need to be balanced against the business harm
to facilitate compliance checking by auditors
likely to result from security issues in the
and business partners.
absence of those controls. The results of a risk
assessment will help guide and determine the
0.5 Lifecycle considerations
appropriate management action and priorities
for managing information security risks and
Information has a natural lifecycle, from crea-
for implementing controls selected to protect
tion and origination through storage, pro-
against these risks.
cessing, use and transmission to its eventual
destruction or decay. The value of, and risks to,
[11]
ISO/IEC 27005 provides information security
assets may vary during their lifetime (e.g. unau-
risk management guidance, including advice on
thorized disclosure or theft of a company’s
risk assessment, risk treatment, risk accept-
financial accounts is far less significant after
ance, risk communication, risk monitoring and
they have been formally published) but infor-
risk review.
mation security remains important to some
extent at all stages.
0.3 Selecting controls
Information systems have lifecycles within
Controls can be selected from this standard or
which they are conceived, specified, designed,
from other control sets, or new controls can be
developed, tested, implemented, used, main-
designed to meet specific needs as appropriate.
tained and eventually retired from service and
The selection of controls is dependent upon
disposed of. Information security should be
organizational decisions based on the criteria
taken into account at every stage. New system
for risk acceptance, risk treatment options and
developments and changes to existing systems
the general risk management approach applied
present opportunities for organizations to
to the organization, and should also be sub-
update and improve security controls, taking
ject to all relevant national and international
actual incidents and current and projected
legislation and regulations. Control selection
information security risks into account.
also depends on the manner in which controls
0.6 Related standards
interact to provide defence in depth.
While this standard offers guidance on a
Some of the controls in this standard can be
broad range of information security controls
considered as guiding principles for information
that are commonly applied in many different
security management and applicable for most
organizations, the remaining standards in the
organizations. The controls are explained in
ISO/IEC 27000 family provide complementary
more detail below along with implementation
advice or requirements on other aspects of
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
the overall process of managing information ISO/IEC 27000 provides a glossary, formally
security. defining most of the terms used throughout
the ISO/IEC 27000 family of standards, and
Refer to ISO/IEC 27000 for a general introduc-
describes the scope and objectives for each
tion to both ISMSs and the family of standards.
member of the family.
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
1 Scope 4.1 Clauses
Each clause defining security controls contains
This International Standard gives guidelines
one or more main security categories.
for organizational information security stand-
ards and information security management
The order of the clauses in this standard does
practices including the selection, implementa-
not imply their importance. Depending on the
tion and management of controls taking into
circumstances, security controls from any or
consideration the organization’s information
all clauses could be important, therefore each
security risk environment(s).
organization applying this standard should
This International Standard is designed to be identify applicable controls, how important
used by organizations that intend to: these are and their application to individual
business processes. Furthermore, lists in this
a) select controls within the process
standard are not in priority order.
of implementing an Information
Security Management System based on
4.2 Control categories
[10]
ISO/IEC 27001;
Each main security control category contains:
b) implement commonly accepted informa-
tion security controls;
a) a control objective stating what is to be
c) develop their own information security achieved;
management guidelines.
b) one or more controls that can be applied
to achieve the control objective.
2 Normative references
Control descriptions are structured as follows:
The following documents, in whole or in part,
Control
are normatively referenced in this document
and are indispensable for its application. For
Defines the specific control statement, to satisfy
dated references, only the edition cited applies.
the control objective.
For undated references, the latest edition of the
Implementation guidance
referenced document (including any amend-
ments) applies.
Provides more detailed information to support
the implementation of the control and meeting
ISO/IEC 27000, Information technology —
the control objective. The guidance may not be
Security techniques — Information security man-
entirely suitable or sufficient in all situations
agement systems — Overview and vocabulary
and may not fulfil the organization’s specific
control requirements. .
3 Terms and definitions
Other information
For the purposes of this document, the terms
Provides further information that may need to
and definitions given in ISO/IEC 27000 apply.
be considered, for example legal considerations
and references to other standards. If there is
no other information to be provided this part
4 Structure of this standard
is not shown.
This standard contains 14 security control
clauses collectively containing a total of 35
main security categories and 114 controls.
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
At a lower level, the information security policy
5 Information security
should be supported by topic-specific policies,
policies
which further mandate the implementation of
information security controls and are typically
5.1 Management direction for
structured to address the needs of certain tar-
get groups within an organization or to cover
information security
certain topics.
Objective: To provide management direc-
Examples of such policy topics include:
tion and support for information security in
accordance with business requirements and
a) access control (see Clause 9);
relevant laws and regulations.
b) information classification (and handling)
(see 8.2);
5.1.1 Policies for information security
c) physical and environmental security (see
Control
Clause 11);
A set of policies for information security should
d) end user oriented topics such as:
be defined, approved by management, published
1) acceptable use of assets (see 8.1.3);
and communicated to employees and relevant
external parties.
2) clear desk and clear screen (see
11.2.9);
Implementation guidance
3) information transfer (see 13.2.1);
At the highest level, organizations should
define an “information security policy” which 4) mobile devices and teleworking (see
6.2);
is approved by management and which sets
out the organization’s approach to managing
5) restrictions on software installations
its information security objectives.
and use (see 12.6.2);
Information security policies should address
e) backup (see 12.3);
requirements created by:
f) information transfer (see 13.2);
a) business strategy;
g) protection from malware (see 12.2);
b) regulations, legislation and contracts;
h) management of technical vulnerabilities
c) the current and projected information
(see 12.6.1);
security threat environment.
i) cryptographic controls (see Clause 10);
The information security policy should contain
j) communications security (see Clause
statements concerning:
13);
a) definition of information security, objec-
k) privacy and protection of personally
tives and principles to guide all activities
identifiable information (see 18.1.4);
relating to information security;
l) supplier relationships (see Clause 15).
b) assignment of general and specific
responsibilities for information security These policies should be communicated to
employees and relevant external parties in a
management to defined roles;
form that is relevant, accessible and under-
c) processes for handling deviations and
standable to the intended reader, e.g. in the
exceptions.
context of an “information security awareness,
education and training programme” (see 7.2.2).
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
Other information
6 Organization of information
security
The need for internal policies for information
security varies across organizations. Internal
policies are especially useful in larger and more
6.1 Internal organization
complex organizations where those defining
and approving the expected levels of control
Objective: To establish a management frame-
are segregated from those implementing the
work to initiate and control the implementa-
controls or in situations where a policy applies
tion and operation of information security
to many different people or functions in the
within the organization.
organization. Policies for information security
can be issued in a single “information security
6.1.1 Information security roles and
policy” document or as a set of individual but
responsibilities
related documents.
Control
If any of the information security policies are
distributed outside the organization, care
All information security responsibilities should
should be taken not to disclose confidential
be defined and allocated.
information.
Implementation guidance
Some organizations use other terms for
Allocation of information security respon-
these policy documents, such as “Standards”,
sibilities should be done in accordance with
“Directives” or “Rules”.
the information security policies (see 5.1.1).
Responsibilities for the protection of individual
5.1.2 Review of the policies for
assets and for carrying out specific informa-
information security
tion security processes should be identified.
Responsibilities for information security risk
Control
management activities and in particular for
The policies for information security should be
acceptance of residual risks should be defined.
reviewed at planned intervals or if significant
These responsibilities should be supplemented,
changes occur to ensure their continuing suit-
where necessary, with more detailed guidance
ability, adequacy and effectiveness.
for specific sites and information processing
facilities. Local responsibilities for the pro-
Implementation guidance
tection of assets and for carrying out specific
Each policy should have an owner who has
security processes should be defined.
approved management responsibility for the
Individuals with allocated information security
development, review and evaluation of the
responsibilities may delegate security tasks to
policies. The review should include assessing
others. Nevertheless they remain accountable
opportunities for improvement of the organi-
and should determine that any delegated tasks
zation’s policies and approach to managing
have been correctly performed.
information security in response to changes
to the organizational environment, business
Areas for which individuals are responsible
circumstances, legal conditions or technical
should be stated. In particular the following
environment.
should take place:
The review of policies for information security
a) the assets and information security pro-
should take the results of management reviews
cesses should be identified and defined;
into account.
b) the entity responsible for each asset or
Management approval for a revised policy
information security process should be
should be obtained.
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
assigned and the details of this responsi- practicable. Whenever it is difficult to segregate,
bility should be documented (see 8.1.2); other controls such as monitoring of activities,
audit trails and management supervision should
c) authorization levels should be defined
be considered.
and documented;
Other information
d) to be able to fulfil responsibilities in the
information security area the appointed
Segregation of duties is a method for reducing
individuals should be competent in the
the risk of accidental or deliberate misuse of
area and be given opportunities to keep
an organization’s assets.
up to date with developments;
e) coordination and oversight of infor-
6.1.3 Contact with authorities
mation security aspects of supplier
Control
relationships should be identified and
documented.
Appropriate contacts with relevant authorities
Other information
should be maintained.
Many organizations appoint an information
Implementation guidance
security manager to take overall responsibil-
Organizations should have procedures in place
ity for the development and implementation
that specify when and by whom authorities (e.g.
of information security and to support the
law enforcement, regulatory bodies, super-
identification of controls.
visory authorities) should be contacted and
However, responsibility for resourcing and
how identified information security incidents
implementing the controls will often remain
should be reported in a timely manner (e.g. if it
with individual managers. One common prac-
is suspected that laws may have been broken).
tice is to appoint an owner for each asset who
Other information
then becomes responsible for its day-to-day
protection.
Organizations under attack from the Internet
may need authorities to take action against
6.1.2 Segregation of duties
the attack source.
Control
Maintaining such contacts may be a require-
ment to support information security incident
Conflicting duties and areas of responsibility
management (see Clause 16) or the business
should be segregated to reduce opportunities
continuity and contingency planning process
for unauthorized or unintentional modification
(see Clause 17). Contacts with regulatory bod-
or misuse of the organization’s assets.
ies are also useful to anticipate and prepare
for upcoming changes in laws or regulations,
Implementation guidance
which have to be implemented by the organi-
Care should be taken that no single person can zation. Contacts with other authorities include
access, modify or use assets without authori- utilities, emergency services, electricity sup-
zation or detection. The initiation of an event
pliers and health and safety, e.g. fire depart-
should be separated from its authorization. The
ments (in connection with business continuity),
possibility of collusion should be considered in telecommunication providers (in connection
designing the controls. with line routing and availability) and water
suppliers (in connection with cooling facilities
Small organizations may find segregation of
for equipment).
duties difficult to achieve, but the principle
should be applied as far as is possible and
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
Implementation guidance
6.1.4 Contact with special interest
groups
Information security should be integrated
into the organization’s project management
Control
method(s) to ensure that information security
Appropriate contacts with special interest risks are identified and addressed as part of a
groups or other specialist security forums and project. This applies generally to any project
professional associations should be maintained.
regardless of its character, e.g. a project for a
core business process, IT, facility management
Implementation guidance
and other supporting processes. The project
management methods in use should require
Membership in special interest groups or
that:
forums should be considered as a means to:
a) information security objectives are
a) improve knowledge about best practices
included in project objectives;
and stay up to date with relevant secu-
rity information;
b) an information security risk assessment
is conducted at an early stage of the pro-
b) ensure the understanding of the infor-
ject to identify necessary controls;
mation security environment is current
and complete;
c) information security is part of all phases
of the applied project methodology.
c) receive early warnings of alerts, adviso-
ries and patches pertaining to attacks
Information security implications should be
and vulnerabilities;
addressed and reviewed regularly in all pro-
jects. Responsibilities for information secu-
d) gain access to specialist information
rity should be defined and allocated to speci-
security advice;
fied roles defined in the project management
e) share and exchange information about
methods.
new technologies, products, threats or
vulnerabilities;
6.2 Mobile devices and
f) provide suitable liaison points when
teleworking
dealing with information security inci-
dents (see Clause 16).
Objective: To ensure the security of telework-
ing and use of mobile devices.
Other information
Information sharing agreements can be estab-
6.2.1 Mobile device policy
lished to improve cooperation and coordination
Control
of security issues. Such agreements should
identify requirements for the protection of
A policy and supporting security measures
confidential information.
should be adopted to manage the risks intro-
duced by using mobile devices.
6.1.5 Information security in pro-
Implementation guidance
ject management
When using mobile devices, special care should
Control
be taken to ensure that business informa-
Information security should be addressed in tion is not compromised. The mobile device
policy should take into account the risks of
project management, regardless of the type
working with mobile devices in unprotected
of the project.
environments.
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
The mobile device policy should consider: Where the mobile device policy allows the use
of privately owned mobile devices, the policy
a) registration of mobile devices;
and related security measures should also
consider:
b) requirements for physical protection;
a) separation of private and business use
c) restriction of software installation;
of the devices, including using software
d) requirements for mobile device software
to support such separation and protect
versions and for applying patches;
business data on a private device;
e) restriction of connection to information
b) providing access to business information
services;
only after users have signed an end user
agreement acknowledging their duties
f) access controls;
(physical protection, software updat-
g) cryptographic techniques;
ing, etc.), waiving ownership of business
data, allowing remote wiping of data by
h) malware protection;
the organization in case of theft or loss of
i) remote disabling, erasure or lockout;
the device or when no longer authorized
to use the service. This policy needs to
j) backups;
take account of privacy legislation.
k) usage of web services and web apps.
Other information
Care should be taken when using mobile devices
in public places, meeting rooms and other
Mobile device wireless connections are simi-
unprotected areas. Protection should be in
lar to other types of network connection, but
place to avoid the unauthorized access to or have important differences that should be
disclosure of the information stored and pro-
considered when identifying controls. Typical
cessed by these devices, e.g. using cryptographic
differences are:
techniques (see Clause 10) and enforcing use of
a) some wireless security protocols are
secret authentication information (see 9.2.4).
immature and have known weaknesses;
Mobile devices should also be physically pro-
b) information stored on mobile devices
tected against theft especially when left, for
may not be backed-up because of limited
example, in cars and other forms of transport,
network bandwidth or because mobile
hotel rooms, conference centres and meet-
devices may not be connected at the
ing places. A specific procedure taking into
times when backups are scheduled.
account legal, insurance and other security
requirements of the organization should be
Mobile devices generally share common func-
established for cases of theft or loss of mobile
tions, e.g. networking, internet access, e-mail
devices. Devices carrying important, sensitive
and file handling, with fixed use devices.
or critical business information should not be
Information security controls for the mobile
left unattended and, where possible, should be
devices generally consist of those adopted in the
physically locked away, or special locks should
fixed use devices and those to address threats
be used to secure the devices.
raised by their usage outside the organization’s
premises.
Training should be arranged for personnel
using mobile devices to raise their awareness
6.2.2 Teleworking
of the additional risks resulting from this way
of working and the controls that should be
Control
implemented.
A policy and supporting security measures
should be implemented to protect information
© ISO/IEC 2013 – All rights reserved
ISO/IEC 270 02 : 2 013
accessed, processed or stored at teleworking on workstations owned privately by
sites. employees or external party users;
j) malware protection and firewall
Implementation guidance
requirements.
Organizations allowing teleworking activities
The guidelines and arrangements to be con-
should issue a policy that defines the conditions
sidered should include:
and restrictions for using teleworking. Where
deemed applicable and allowed by law, the fol-
a) the provision of suitable equipment and
lowing matters should be considered:
storage furniture for the tel
...
INTERNATIONAL ISO/IEC
STANDARD 27002
Redline version
compares second edition
to first edition
Information technology — Security
techniques — Code of practice for
information security controls
Technologies de l’information — Techniques de sécurité — Code de
bonne pratique pour le management de la sécurité de l’information
Reference number
ISO/IEC 27002:redline:2014(E)
©
ISO/IEC 2014
ISO/IEC 27002:redline:2014(E)
IMPORTANT — PLEASE NOTE
This is a mark-up copy and uses the following colour coding:
Text example 1 — indicates added text (in green)
Text example 2 — indicates removed text (in red)
— indicates added graphic figure
— indicates removed graphic figure
1.x . — Heading numbers containg modifications are highlighted in yellow in
the Table of Contents
DISCLAIMER
This Redline version provides you with a quick and easy way to compare the main changes
between this edition of the standard and its previous edition. It doesn’t capture all single
changes such as punctuation but highlights the modifications providing customers with
the most valuable information. Therefore it is important to note that this Redline version is
not the official ISO standard and that the users must consult with the clean version of the
standard, which is the official standard, for implementation purposes.
© ISO 2014
All rights reserved. Unless otherwise specified, no part of this publication may be reproduced or utilized otherwise in any form
or by any means, electronic or mechanical, including photocopying, or posting on the internet or an intranet, without prior
written permission. Permission can be requested from either ISO at the address below or ISO’s member body in the country of
the requester.
ISO copyright office
Case postale 56 • CH-1211 Geneva 20
Tel. + 41 22 749 01 11
Fax + 41 22 749 09 47
E-mail copyright@iso.org
Web www.iso.org
Published in Switzerland
ii © ISO 2014 – All rights reserved
ISO/IEC 27002:redline:2014(E)
Contents Page
Foreword .vi
Foreword .vii
0 Introduction .viii
0.1 What is information security? .viii
0.2 Why information security is needed? .viii
0.3 How to establish security requirements . ix
0.4 Assessing security risks . ix
0.5 Selecting controls . ix
0.6 Information security starting point .x
0.7 Critical success factors .x
0.8 Developing your own guidelines . xi
1 Scope . 1
2 Normative references . 1
2 3 Terms and definitions . 1
3 4 Structure of this standard .3
3.1 4.1 Clauses . 3
3.2 4.2 Main security Control categories . 4
4 Risk assessment and treatment . 4
4.1 Assessing security risks . 4
4.2 Treating security risks . 5
5 Security policy Information security policies . 6
5.1 Information security policy Management direction for information security . 6
6 Organization of information security . 8
6.1 Internal organization . 8
6.2 External parties .13
7 Asset management .18
7.1 Responsibility for assets .18
7.2 Information classification .20
8 Human resources security.21
8.1 Prior to employment .21
8.2 During employment .23
8.3 Termination or change of employment .24
9 Physical and environmental security .26
9.1 Secure areas .26
9.2 Equipment security .29
10 Communications and operations management .33
10.1 Operational procedures and responsibilities .33
10.2 Third party service delivery management .35
10.3 System planning and acceptance .37
10.4 Protection against malicious and mobile code .38
10.5 Back-up .40
10.6 Network security management .40
10.7 Media handling .42
10.8 Exchange of information.44
10.9 Electronic commerce services .48
10.10 Monitoring .50
11 6 Access control Organization of information security .54
11.1 Business requirement for access control .54
11.2 User access management .55
ISO/IEC 27002:redline:2014(E)
11.3 User responsibilities .57
11.4 6.1 . Network access
control Internal organization .59
11.5 Operating system access control .64
11.6 Application and information access control .68
11.7 6.2 . Mobile computing devices
and teleworking .69
7 Human resource security .72
7.1 Prior to employment .72
7.2 During employment .73
7.3 Termination and change of employment .76
8 Asset management .76
8.1 Responsibility for assets .76
8.2 Information classification .78
8.3 Media handling .80
9 Access control .82
9.1 Business requirements of access control .82
9.2 User access management .84
9.3 User responsibilities .87
9.4 System and application access control .88
10 Cryptography .91
10.1 Cryptographic controls .91
11 Physical and environmental security .94
11.1 Secure areas .94
11.2 Equipment .97
12 Operations security .101
12.1 Operational procedures and responsibilities .101
12.2 Protection from malware .104
12.3 Backup .106
12.4 Logging and monitoring .106
12.5 Control of operational software .109
12.6 Technical vulnerability management .109
12.7 Information systems audit considerations .111
13 Communications security .112
13.1 Network security management .112
13.2 Information transfer .114
12 14 Information systems System acquisition, development and maintenance .117
12.1 14.1 . Security requirements of
information systems .117
12.2 Correct processing in applications .120
12.3 Cryptographic controls .122
12.4 Security of system files .125
12.5 14.2 . Security in development and
support processes .127
12.6 14.3 . Technical Vulnerability
Management Test data .132
15 Supplier relationships .134
15.1 Information security in supplier relationships .134
15.2 Supplier service delivery management .137
13 16 Information security incident management .139
13.1 Reporting information security events and weaknesses .139
13.2 16.1 . Management of information security incidents
and improvements .140
iv © ISO 2014 – All rights reserved
ISO/IEC 27002:redline:2014(E)
14 17 Business Information security aspects of business continuity management.145
14.1 17.1 . Information security aspects of business continuity
management continuity .145
17.2 Redundancies .150
15 18 Compliance .151
15.1 18.1 .Compliance with legal and
contractual requirements .151
15.2 18.2 . Compliance with security policies and standards, and technical compliance Information
security reviews .155
15.3 Information systems audit considerations .157
Bibliography .158
ISO/IEC 27002:redline:2014(E)
Foreword
ISO (the International Organization for Standardization) and IEC (the International Electrotechnical
Commission) form the specialized system for worldwide standardization. National bodies that are
members of ISO or IEC participate in the development of International Standards through technical
committees established by the respective organization to deal with particular fields of technical
activity. ISO and IEC technical committees collaborate in fields of mutual interest. Other international
organizations, governmental and non-governmental, in liaison with ISO and IEC, also take part in the
work. In the field of information technology, ISO and IEC have established a joint technical committee,
ISO/IEC JTC 1.
International Standards are drafted in accordance with the rules given in the ISO/IEC Directives, Part 2.
TheISO/IEC 27002 main task of the joint technical committee is to prepare International Standards.
Draft International Standards adopted by the joint technical committeewas prepared by Joint Technical
Committee ISO/IEC JTC 1, are circulatedInformation technology to national bodies, Subcommittee SC
27, for voting. Publication IT Security techniquesas an International Standard requires approval by at
least 75 % of the national bodies casting a vote.
Attention is drawn to the possibility that some of the elements of this document may be the subject of
patent rights. ISO and IEC shall not be held responsible for identifying any or all such patent rights.
ISO/IEC 27002 was prepared by Joint Technical Committee ISO/IEC JTC 1, Information technology,
Subcommittee SC 27, IT Security techniques.
This first edition ofsecond edition cancels and replaces the first edition (ISO/IEC 27002:2005), ISO/IEC 27002
compriseswhich has ISO/IEC 17799:2005been technically and ISO/IEC 17799:2005/Cor.1:2007. It s technical
content is identical to that of structurally revisedISO/IEC 17799:2005.ISO/IEC 17799:2005/Cor.1:2007
changes the reference number of the standard from 17799 to 27002. ISO/IEC 17799:2005 and
ISO/IEC 17799:2005/Cor.1:2007 are provisionally retained until publication of the second edition of
ISO/IEC 27002.
vi © ISO 2014 – All rights reserved
ISO/IEC 27002:redline:2014(E)
Foreword
ISO (the International Organization for Standardization) and IEC (the International Electrotechnical
Commission) form the specialized system for worldwide standardization. National bodies that are
members of ISO or IEC participate in the development of International Standards through technical
committees established by the respective organization to deal with particular fields of technical
activity. ISO and IEC technical committees collaborate in fields of mutual interest. Other international
organizations, governmental and non-governmental, in liaison with ISO and IEC, also take part in the
work. In the field of information technology, ISO and IEC have established a joint technical committee,
ISO/IEC JTC 1.
International Standards are drafted in accordance with the rules given in the ISO/IEC Directives, Part 2.
The main task of the joint technical committee is to prepare International Standards. Draft International
Standards adopted by the joint technical committee are circulated to national bodies for voting.
Publication as an International Standard requires approval by at least 75 % of the national bodies
casting a vote.
Attention is drawn to the possibility that some of the elements of this document may be the subject of
patent rights. ISO and IEC shall not be held responsible for identifying any or all such patent rights.
ISO/IEC 17799 was prepared by Joint Technical Committee ISO/IEC JTC 1, Information technology,
Subcommittee SC 27, IT Security techniques.
This second edition cancels and replaces the first edition (ISO/IEC 17799:2000), which has been
technically revised.
A family of Information Security Management System (ISMS) International Standards is being developed
within ISO/IEC JTC 1/SC 27. The family includes International Standards on information security
management system requirements, risk management, metrics and measurement, and implementation
guidance. This family will adopt a numbering scheme using the series of numbers 27000 et seq.
From 2007, it is proposed to incorporate the new edition of ISO/IEC 17799 into this new numbering
scheme as ISO/IEC 27002.
ISO/IEC 27002:redline:2014(E)
0 Introduction
0.1 What is information security?
Information is an asset that, like other important business assets, is essential to an organization’s
business and consequently needs to be suitably protected. This is especially important in the increasingly
interconnected business environment. As a result of this increasing interconnectivity, information is
now exposed to a growing number and a wider variety of threats and vulnerabilities (see also OECD
Guidelines for the Security of Information Systems and Networks).
Information can exist in many forms. It can be printed or written on paper, stored electronically, transmitted
by post or by using electronic means, shown on films, or spoken in conversation. Whatever form the
information takes, or means by which it is shared or stored, it should always be appropriately protected.
Information security is the protection of information from a wide range of threats in order to ensure
business continuity, minimize business risk, and maximize return on investments and business
opportunities.
Information security is achieved by implementing a suitable set of controls, including policies, processes,
procedures, organizational structures and software and hardware functions. These controls need to
be established, implemented, monitored, reviewed and improved, where necessary, to ensure that the
specific security and business objectives of the organization are met. This should be done in conjunction
with other business management processes.
0.1 Background and context
0.2 Why information security is needed?
Information and the supporting processes, systems, and networks are important business assets.
Defining, achieving, maintaining, and improving information security may be essential to maintain
competitive edge, cash flow, profitability, legal compliance, and commercial image.
Organizations and their information systems and networks are faced with security threats from a
wide range of sources, including computer-assisted fraud, espionage, sabotage, vandalism, fire or flood.
Causes of damage such as malicious code, computer hacking, and denial of service attacks have become
more common, more ambitious, and increasingly sophisticated.
Information security is important to both public and private sector businesses, and to protect critical
infrastructures. In both sectors, information security will function as an enabler, e.g. to achieve
e-government or e-business, and to avoid or reduce relevant risks. The interconnection of public and private
networks and the sharing of information resources increase the difficulty of achieving access control. The
trend to distributed computing has also weakened the effectiveness of central, specialist control.
Many information systems have not been designed to be secure. The security that can be achieved
through technical means is limited, and should be supported by appropriate management and
procedures. Identifying which controls should be in place requires careful planning and attention to
detail. Information security management requires, as a minimum, participation by all employees in the
organization. It may also require participation from shareholders, suppliers, third parties, customers or
other external parties. Specialist advice from outside organizations may also be needed.
This International Standard is designed for organizations to use as a reference for selecting controls
within the process of implementing an Information Security Management System (ISMS) based on
[10]
ISO/IEC 27001 or as a guidance document for organizations implementing commonly accepted
information security controls. This standard is also intended for use in developing industry- and
organization-specific information security management guidelines, taking into consideration their
specific information security risk environment(s).
viii © ISO 2014 – All rights reserved
ISO/IEC 27002:redline:2014(E)
0.3 How to establish security requirements
It is essential that an organization identifies its security requirements. There are three main sources of
security requirements.
1) One source is derived from assessing risks to the organization, taking into account the organization’s
overall business strategy and objectives. Through a risk assessment, threats to assets are identified,
vulnerability to and likelihood of occurrence is evaluated and potential impact is estimated.
2) Another source is the legal, statutory, regulatory, and contractual requirements that an
organization, its trading partners, contractors, and service providers have to satisfy, and their
socio-cultural environment.
3) A further source is the particular set of principles, objectives and business requirements for
information processing that an organization has developed to support its operations.
Organizations of all types and sizes (including public and private sector, commercial and non-profit)
collect, process, store and transmit information in many forms including electronic, physical and verbal
(e.g. conversations and presentations).
0.4 Assessing security risks
Security requirements are identified by a methodical assessment of security risks. Expenditure on
controls needs to be balanced against the business harm likely to result from security failures.
The results of the risk assessment will help to guide and determine the appropriate management action
and priorities for managing information security risks, and for implementing controls selected to
protect against these risks.
Risk assessment should be repeated periodically to address any changes that might influence the risk
assessment results.
More information about the assessment of security risks can be found in clause 4.1 “Assessing security risks”.
The value of information goes beyond the written words, numbers and images: knowledge, concepts, ideas
and brands are examples of intangible forms of information. In an interconnected world, information and
related processes, systems, networks and personnel involved in their operation, handling and protection
are assets that, like other important business assets, are valuable to an organization’s business and
consequently deserve or require protection against various hazards.
0.5 Selecting controls
Once security requirements and risks have been identified and decisions for the treatment of risks have
been made, appropriate controls should be selected and implemented to ensure risks are reduced to an
acceptable level. Controls can be selected from this standard or from other control sets, or new controls
can be designed to meet specific needs as appropriate. The selection of security controls is dependent
upon organizational decisions based on the criteria for risk acceptance, risk treatment options, and the
general risk management approach applied to the organization, and should also be subject to all relevant
national and international legislation and regulations.
Some of the controls in this standard can be considered as guiding principles for information security
management and applicable for most organizations. They are explained in more detail below under the
heading “Information security starting point”.
More information about selecting controls and other risk treatment options can be found in clause 4.2
“Treating security risks”.
Assets are subject to both deliberate and accidental threats while the related processes, systems,
networks and people have inherent vulnerabilities. Changes to business processes and systems or
other external changes (such as new laws and regulations) may create new information security risks.
ISO/IEC 27002:redline:2014(E)
Therefore, given the multitude of ways in which threats could take advantage of vulnerabilities to harm
the organization, information security risks are always present. Effective information security reduces
these risks by protecting the organization against threats and vulnerabilities, and then reduces impacts
to its assets.
0.6 Information security starting point
A number of controls can be considered as a good starting point for implementing information security.
They are either based on essential legislative requirements or considered to be common practice for
information security.
Controls considered to be essential to an organization from a legislative point of view include, depending
on applicable legislation:
a) data protection and privacy of personal information (see 15.1.4);
b) protection of organizational records (see 15.1.3);
c) intellectual property rights (see 15.1.2).
Controls considered to be common practice for information security include:
a) information security policy document (see 5.1.1);
b) allocation of information security responsibilities (see 6.1.3);
c) information security awareness, education, and training (see 8.2.2);
d) correct processing in applications (see 12.2);
e) technical vulnerability management (see 12.6);
f) business continuity management (see 14);
g) management of information security incidents and improvements (see 13.2).
These controls apply to most organizations and in most environments.
It should be noted that although all controls in this standard are important and should be considered, the
relevance of any control should be determined in the light of the specific risks an organization is facing.
Hence, although the above approach is considered a good starting point, it does not replace selection of
controls based on a risk assessment.
Information security is achieved by implementing a suitable set of controls, including policies, processes,
procedures, organizational structures and software and hardware functions. These controls need to
be established, implemented, monitored, reviewed and improved, where necessary, to ensure that the
specific security and business objectives of the organization are met. An ISMS such as that specified in
[10]
ISO/IEC 27001 takes a holistic, coordinated view of the organization’s information security risks in
order to implement a comprehensive suite of information security controls under the overall framework
of a coherent management system.
0.7 Critical success factors
Experience has shown that the following factors are often critical to the successful implementation of
information security within an organization:
a) information security policy, objectives, and activities that reflect business objectives;
b) an approach and framework to implementing, maintaining, monitoring, and improving information
security that is consistent with the organizational culture;
c) visible support and commitment from all levels of management;
x © ISO 2014 – All rights reserved
ISO/IEC 27002:redline:2014(E)
d) a good understanding of the information security requirements, risk assessment, and risk management;
e) effective marketing of information security to all managers, employees, and other parties to
achieve awareness;
f) distribution of guidance on information security policy and standards to all managers, employees
and other parties;
g) provision to fund information security management activities;
h) providing appropriate awareness, training, and education;
i) establishing an effective information security incident management process;
1)
j) implementation of a measurement system that is used to evaluate performance in information
security management and feedback suggestions for improvement.
[10]
Many information systems have not been designed to be secure in the sense of ISO/IEC 27001 and this
standard. The security that can be achieved through technical means is limited and should be supported
by appropriate management and procedures. Identifying which controls should be in place requires
careful planning and attention to detail. A successful ISMS requires support by all employees in the
organization. It can also require participation from shareholders, suppliers or other external parties.
Specialist advice from external parties can also be needed.
0.8 Developing your own guidelines
This code of practice may be regarded as a starting point for developing organization specific guidelines.
Not all of the controls and guidance in this code of practice may be applicable. Furthermore, additional
controls and guidelines not included in this standard may be required. When documents are developed
containing additional guidelines or controls, it may be useful to include cross-references to clauses in
this standard where applicable to facilitate compliance checking by auditors and business partners.
In a more general sense, effective information security also assures management and other stakeholders
that the organization’s assets are reasonably safe and protected against harm, thereby acting as a
business enabler.
0.2 Information security requirements
It is essential that an organization identifies its security requirements. There are three main sources of
security requirements:
a) the assessment of risks to the organization, taking into account the organization’s overall business
strategy and objectives. Through a risk assessment, threats to assets are identified, vulnerability to
and likelihood of occurrence is evaluated and potential impact is estimated;
b) the legal, statutory, regulatory and contractual requirements that an organization, its trading
partners, contractors and service providers have to satisfy, and their socio-cultural environment;
c) the set of principles, objectives and business requirements for information handling, processing,
storing, communicating and archiving that an organization has developed to support its operations.
Resources employed in implementing controls need to be balanced against the business harm likely
to result from security issues in the absence of those controls. The results of a risk assessment will
help guide and determine the appropriate management action and priorities for managing information
security risks and for implementing controls selected to protect against these risks.
[11]
ISO/IEC 27005 provides information security risk management guidance, including advice on risk
assessment, risk treatment, risk acceptance, risk communication, risk monitoring and risk review.
0.3 Selecting controls
1) Note that information security measurements are outside of the scope of this standard.
ISO/IEC 27002:redline:2014(E)
Controls can be selected from this standard or from other control sets, or new controls can be designed
to meet specific needs as appropriate.
The selection of controls is dependent upon organizational decisions based on the criteria for risk
acceptance, risk treatment options and the general risk management approach applied to the organization,
and should also be subject to all relevant national and international legislation and regulations. Control
selection also depends on the manner in which controls interact to provide defence in depth.
Some of the controls in this standard can be considered as guiding principles for information security
management and applicable for most organizations. The controls are explained in more detail below
along with implementation guidance. More information about selecting controls and other risk treatment
[11]
options can be found in ISO/IEC 27005.
0.4 Developing your own guidelines
This International Standard may be regarded as a starting point for developing organization-specific
guidelines. Not all of the controls and guidance in this code of practice may be applicable. Furthermore,
additional controls and guidelines not included in this standard may be required. When documents are
developed containing additional guidelines or controls, it may be useful to include cross-references to clauses
in this standard where applicable to facilitate compliance checking by auditors and business partners.
0.5 Lifecycle considerations
Information has a natural lifecycle, from creation and origination through storage, processing, use and
transmission to its eventual destruction or decay. The value of, and risks to, assets may vary during their
lifetime (e.g. unauthorized disclosure or theft of a company’s financial accounts is far less significant after
they have been formally published) but information security remains important to some extent at all stages.
Information systems have lifecycles within which they are conceived, specified, designed, developed,
tested, implemented, used, maintained and eventually retired from service and disposed of. Information
security should be taken into account at every stage. New system developments and changes to existing
systems present opportunities for organizations to update and improve security controls, taking actual
incidents
...
NORME ISO/CEI
INTERNATIONALE 27002
Deuxième édition
2013-10-01
Technologies de l’information —
Techniques de sécurité — Code de
bonne pratique pour le management
de la sécurité de l’information
Information technology — Security techniques — Code of practice for
information security controls
Numéro de référence
ISO/CEI 27002:2013(F)
©
ISO/CEI 2013
ISO/CEI 27002:2013(F)
DOCUMENT PROTÉGÉ PAR COPYRIGHT
© ISO/CEI 2013
Droits de reproduction réservés. Sauf indication contraire, aucune partie de cette publication ne peut être reproduite ni utilisée
sous quelque forme que ce soit et par aucun procédé, électronique ou mécanique, y compris la photocopie, l’affichage sur
l’internet ou sur un Intranet, sans autorisation écrite préalable. Les demandes d’autorisation peuvent être adressées à l’ISO à
l’adresse ci-après ou au comité membre de l’ISO dans le pays du demandeur.
ISO copyright office
Case postale 56 • CH-1211 Geneva 20
Tel. + 41 22 749 01 11
Fax + 41 22 749 09 47
E-mail copyright@iso.org
Web www.iso.org
Publié en Suisse
ii © ISO/CEI 2013 – Tous droits réservés
ISO/CEI 27002:2013(F)
Sommaire Page
Avant-propos .v
0 Introduction .vi
1 Domaine d’application . 1
2 Références normatives . 1
3 Termes et définitions . 1
4 Structure de la présente norme . 1
4.1 Articles . 1
4.2 Catégories de mesures . 2
5 Politiques de sécurité de l’information . 2
5.1 Orientations de la direction en matière de sécurité de l’information . 2
6 Organisation de la sécurité de l’information . 4
6.1 Organisation interne . 4
6.2 Appareils mobiles et télétravail . 7
7 La sécurité des ressources humaines . 9
7.1 Avant l’embauche . 9
7.2 Pendant la durée du contrat .11
7.3 Rupture, terme ou modification du contrat de travail .14
8 Gestion des actifs.15
8.1 Responsabilités relatives aux actifs .15
8.2 Classification de l’information .16
8.3 Manipulation des supports . .19
9 Contrôle d’accès .21
9.1 Exigences métier en matière de contrôle d’accès .21
9.2 Gestion de l’accès utilisateur .23
9.3 Responsabilités des utilisateurs .27
9.4 Contrôle de l’accès au système et aux applications .28
10 Cryptographie .31
10.1 Mesures cryptographiques .31
11 Sécurité physique et environnementale .34
11.1 Zones sécurisées .34
11.2 Matériels .37
12 Sécurité liée à l’exploitation .42
12.1 Procédures et responsabilités liées à l’exploitation.42
12.2 Protection contre les logiciels malveillants .46
12.3 Sauvegarde .47
12.4 Journalisation et surveillance .48
12.5 Maîtrise des logiciels en exploitation .50
12.6 Gestion des vulnérabilités techniques .51
12.7 Considérations sur l’audit du système d’information .53
13 Sécurité des communications .54
13.1 Management de la sécurité des réseaux .54
13.2 Transfert de l’information .56
14 Acquisition, développement et maintenance des systèmes d’information .60
14.1 Exigences de sécurité applicables aux systèmes d’information .60
14.2 Sécurité des processus de développement et d’assistance technique .63
14.3 Données de test .68
15 Relations avec les fournisseurs .69
15.1 Sécurité de l’information dans les relations avec les fournisseurs .69
© ISO/CEI 2013 – Tous droits réservés iii
ISO/CEI 27002:2013(F)
15.2 Gestion de la prestation du service .72
16 Gestion des incidents liés à la sécurité de l’information .74
16.1 Gestion des incidents liés à la sécurité de l’information et améliorations .74
17 Aspects de la sécurité de l’information dans la gestion de la continuité de l’activité .78
17.1 Continuité de la sécurité de l’information .78
17.2 Redondances .80
18 Conformité .81
18.1 Conformité aux obligations légales et réglementaires .81
18.2 Revue de la sécurité de l’information .84
Bibliographie .87
iv © ISO/CEI 2013 – Tous droits réservés
ISO/CEI 27002:2013(F)
Avant-propos
L’ISO (Organisation internationale de normalisation) et la CEI (Commission électrotechnique
internationale) forment le système spécialisé de la normalisation mondiale. Les organismes nationaux
membres de l’ISO ou de la CEI participent au développement de Normes internationales par l’intermédiaire
des comités techniques créés par l’organisation concernée afin de s’occuper des domaines particuliers
de l’activité technique. Les comités techniques de l’ISO et de la CEI collaborent dans des domaines
d’intérêt commun. D’autres organisations internationales, gouvernementales et non gouvernementales,
en liaison avec l’ISO et la CEI participent également aux travaux. Dans le domaine des technologies de
l’information, l’ISO et la CEI ont créé un comité technique mixte, l’ISO/CEI JTC 1.
Les Normes internationales sont rédigées conformément aux règles données dans les Directives
ISO/CEI, Partie 2.
La tâche principale du comité technique mixte est d’élaborer les Normes internationales. Les projets de
Normes internationales adoptés par le comité technique mixte sont soumis aux organismes nationaux
pour vote. Leur publication comme Normes internationales requiert l’approbation de 75 % au moins des
organismes nationaux votants.
L’attention est appelée sur le fait que certains des éléments du présent document peuvent faire l’objet de
droits de propriété intellectuelle ou de droits analogues. L’ISO ne saurait être tenue pour responsable de
ne pas avoir identifié de tels droits de propriété et averti de leur existence.
L’ISO/CEI 27002 a été élaborée par le comité technique ISO/CEI TC JTC 1, Technologies de l’information,
sous-comité SC 27, Techniques de sécurité des technologies de l’information.
Cette deuxième édition annule et remplace la première édition (ISO/CEI 27002:2005), qui a fait l’objet
d’une révision technique et structurelle.
© ISO/CEI 2013 – Tous droits réservés v
ISO/CEI 27002:2013(F)
0 Introduction
0.1 Historique et contexte
La présente Norme internationale a pour objet de servir d’outil de référence permettant aux
organisations de sélectionner les mesures nécessaires dans le cadre d’un processus de mise en œuvre
[10]
d’un système de management de la sécurité de l’information (SMSI) selon l’ISO/CEI 27001 ou de
guide pour les organisations mettant en œuvre des mesures de sécurité de l’information largement
reconnues. La présente norme a également pour objet d’élaborer des lignes directrices de management
de la sécurité de l’information spécifiques aux organisations et aux entreprises, en tenant compte de
leur(s) environnement(s) particulier(s) de risques de sécurité de l’information.
Des organisations de tous types et de toutes dimensions (incluant le secteur public et le secteur privé, à but
lucratif ou non lucratif) collectent, traitent, stockent et transmettent l’information sous de nombreuses
formes, notamment électronique, physique et verbale (par exemple, au cours de conversations et de
présentations).
La valeur de l’information dépasse les mots, les chiffres et les images: la connaissance, les concepts,
les idées et les marques sont des exemples de formes d’information immatérielles. Dans un monde
interconnecté, l’information et les processus, systèmes et réseaux qui s’y rattachent, ainsi que le
personnel impliqué dans son traitement, ses manipulations et sa protection, sont des actifs précieux
pour l’activité d’une organisation, au même titre que d’autres actifs d’entreprise importants, et, par
conséquent, ils méritent ou nécessitent d’être protégés contre les divers risques encourus.
Les actifs sont exposés à des menaces tant accidentelles que délibérées, alors que les processus, les
systèmes, les réseaux et les personnes qui s’y rattachent présentent des vulnérabilités qui leur sont
propres. Des changements apportés aux processus et aux systèmes de l’organisation ou d’autres
changements externes (comme l’application de nouvelles lois et réglementations) peuvent engendrer
de nouveaux risques pour la sécurité de l’information. Par conséquent, étant donné que les menaces
disposent d’une multitude de possibilités d’exploitation des vulnérabilités pour nuire à l’organisation,
les risques de sécurité de l’information sont omniprésents. Une sécurité efficace de l’information réduit
ces risques en protégeant l’organisation contre les menaces et les vulnérabilités, ce qui réduit les
conséquences sur ses actifs.
La sécurité de l’information est assurée par la mise en œuvre de mesures adaptées, qui regroupent des
règles, des processus, des procédures, des structures organisationnelles et des fonctions matérielles
et logicielles. Ces mesures doivent être spécifiées, mises en œuvre, suivies, réexaminées et améliorées
aussi souvent que nécessaire, de manière à atteindre les objectifs spécifiques en matière de sécurité et
d’activité d’une organisation. Un système de management de la sécurité de l’information (SMSI) tel que
[10]
celui spécifié dans l’ISO/CEI 27001 appréhende les risques de sécurité de l’information de l’organisation
dans une vision globale et coordonnée, de manière à mettre en œuvre un ensemble complet de mesures
liées à la sécurité de l’information dans le cadre général d’un système de management cohérent.
Nombreux sont les systèmes d’information qui n’ont pas été conçus dans un souci de sécurité au sens
[10]
de l’ISO/CEI 27001 et de la présente norme. La sécurité qui peut être mise en œuvre par des moyens
techniques est limitée et il convient de la soutenir à l’aide de moyens de management et de procédures
adaptés. L’identification des mesures qu’il convient de mettre en place nécessite de procéder à une
planification minutieuse et de prêter attention aux détails. Un système de management de la sécurité
de l’information efficace requiert l’adhésion de tous les salariés de l’organisation. Il peut également
nécessiter la participation des actionnaires, des fournisseurs ou d’autres tiers. De même, l’avis de
spécialistes tiers peut se révéler nécessaire.
De manière plus générale, une sécurité de l’information efficace garantit également à la direction et aux
parties tiers que les actifs de l’organisation sont, dans des limites raisonnables, sécurisés et à l’abri des
préjudices, et contribuent de ce fait au succès de l’organisation.
0.2 Exigences liées à la sécurité de l’information
vi © ISO/CEI 2013 – Tous droits réservés
ISO/CEI 27002:2013(F)
Une organisation doit impérativement identifier ses exigences en matière de sécurité. Ces exigences
proviennent de trois sources principales:
a) l’appréciation du risque propre à l’organisation, prenant en compte sa stratégie et ses objectifs
généraux. L’appréciation du risque permet d’identifier les menaces pesant sur les actifs, d’analyser
les vulnérabilités, de mesurer la vraisemblance des attaques et d’en évaluer l’impact potentiel;
b) les exigences légales, statutaires, réglementaires et contractuelles auxquelles l’organisation et ses
partenaires commerciaux, contractants et prestataires de service, doivent répondre ainsi que leur
environnement socioculturel;
c) l’ensemble de principes, d’objectifs et d’exigences métier en matière de manipulation, de traitement,
de stockage, de communication et d’archivage de l’information que l’organisation s’est constitué
pour mener à bien ses activités.
Il est nécessaire de confronter les ressources mobilisées par la mise en œuvre des mesures avec les
dommages susceptibles de résulter de défaillances de la sécurité en l’absence de ces mesures. Les
résultats d’une appréciation du risque permettent de définir les actions de gestion appropriées et les
priorités en matière de gestion des risques liés à la sécurité de l’information, ainsi que de mettre en
œuvre les mesures identifiées destinées à contrer ces risques.
[11]
La norme ISO/CEI 27005 fournit des lignes directrices de gestion du risque lié à la sécurité de
l’information, y compris des conseils sur l’appréciation du risque, le traitement du risque, l’acceptation
du risque, la communication relative au risque, la surveillance du risque et la revue du risque.
0.3 Sélection des mesures
Selon les cas, il est possible de sélectionner les mesures dans la présente norme ou dans d’autres guides,
ou encore de spécifier de nouvelles mesures en vue de satisfaire des besoins spécifiques.
La sélection des mesures dépend des décisions prises par l’organisation en fonction de ses critères
d’acceptation du risque, de ses options de traitement du risque et de son approche de la gestion générale
du risque. Il convient également de prendre en considération les lois et règlements nationaux et
internationaux concernés. La sélection des mesures de sécurité dépend également de la manière dont
les mesures interagissent pour assurer une défense en profondeur.
Certaines mesures décrites dans la présente norme peuvent être considérées comme des principes
directeurs pour le management de la sécurité de l’information et être appliquées à la plupart des
organisations. Les mesures et des lignes directrices de mise en œuvre sont détaillées ci-dessous. De plus
amples informations sur la sélection des mesures et d’autres options de traitement du risque figurent
[11]
dans l’ISO/CEI 27005.
0.4 Mise au point de lignes directrices propres à l’organisation
La présente Norme internationale peut servir de base pour la mise au point de lignes directrices
spécifiques à une organisation. Une partie des mesures et lignes directrices de ce code de bonnes
pratiques peut ne pas être applicable. Par ailleurs, des mesures et des lignes directrices ne figurant
pas dans la présente norme peuvent être nécessaires. Lors de la rédaction de documents contenant des
lignes directrices ou des mesures supplémentaires, il peut être utile d’intégrer des références croisées
aux articles de la présente norme, le cas échéant, afin de faciliter la vérification de la conformité par les
auditeurs et les partenaires commerciaux.
0.5 Examen du cycle de vie
L’information est soumise à un cycle de vie naturel, depuis sa création et son origine en passant par
son stockage, son traitement, son utilisation, sa transmission, jusqu’à sa destruction finale ou son
obsolescence. La valeur des actifs et les risques qui y sont liés peuvent varier au cours de la durée de
vie de ces actifs (par exemple, une divulgation non autorisée ou le vol des comptes financiers d’une
entreprise revêt une importance bien moins grande après leur publication officielle), mais dans une
certaine mesure l‘importance de la sécurité de l’information subsiste à tous les stades.
© ISO/CEI 2013 – Tous droits réservés vii
ISO/CEI 27002:2013(F)
Les systèmes d’information sont soumis à des cycles de vie durant lesquels ils sont pensés, caractérisés,
conçus, mis au point, testés, mis en œuvre, utilisés, entretenus et finalement retirés du service et mis
au rebut. Il convient que la sécurité de l’information soit prise en compte à tous les stades. La mise au
point de nouveaux systèmes et les changements apportés aux systèmes existants donnent l’occasion
aux organisations de mettre à jour les mesures de sécurité et de les améliorer en tenant compte des
incidents réels survenus et des risques de sécurité de l’information actuels et anticipés.
0.6 Normes associées
Alors que la présente Norme internationale propose des lignes directrices portant sur un vaste éventail
de mesures de sécurité liées à l’information d’utilisation courante dans nombre d’organisations
différentes, les autres normes de la famille ISO/CEI 27000 présentent des conseils complémentaires ou
des exigences relatifs à d’autres aspects de l’ensemble du processus de management de la sécurité de
l’information.
Se reporter à l’ISO/CEI 27000 pour une introduction générale aux systèmes de management de la
sécurité de l’information et à la famille de normes. L’ISO/CEI 27000 présente un glossaire, définissant
de manière formelle la plupart des termes utilisés dans la famille de normes ISO/CEI 27000, et décrit le
domaine d’application et les objectifs de chaque élément de cette famille.
viii © ISO/CEI 2013 – Tous droits réservés
NORME INTERNATIONALE ISO/CEI 27002:2013(F)
Technologies de l’information — Techniques de sécurité —
Code de bonne pratique pour le management de la sécurité
de l’information
1 Domaine d’application
La présente Norme internationale donne des lignes directrices en matière de normes organisationnelles
relatives à la sécurité de l’information et des bonnes pratiques de management de la sécurité de
l’information, incluant la sélection, la mise en œuvre et la gestion de mesures de sécurité prenant en
compte le ou les environnement(s) de risques de sécurité de l’information de l’organisation.
La présente Norme internationale est élaborée à l’intention des organisations désireuses
a) de sélectionner les mesures nécessaires dans le cadre du processus de mise en œuvre d’un système
[10]
de management de la sécurité de l’information (SMSI) selon l’ISO/CEI 27001;
b) de mettre en œuvre des mesures de sécurité de l’information largement reconnues;
c) d’élaborer leurs propres lignes directrices de management de la sécurité de l’information.
2 Références normatives
Les documents suivants, en tout ou partie, sont référencés de manière normative dans le présent
document et sont indispensables à son application. Pour les références datées, seule l’édition citée
s’applique. Pour les références non datées, la dernière édition du document de référence s’applique (y
compris les éventuels amendements).
ISO/CEI 27000, Technologies de l’information — Techniques de sécurité — Systèmes de management de la
sécurité de l’information — Vue d’ensemble et vocabulaire
3 Termes et définitions
Pour les besoins du présent document, les termes et définitions donnés dans l’ISO/CEI 27000 s’appliquent.
4 Structure de la présente norme
La présente norme contient 14 articles relatifs aux mesures de sécurité, comprenant un total de
35 catégories de sécurité principales et 114 mesures.
4.1 Articles
Chaque article définissant des mesures de sécurité contient une ou plusieurs catégories de sécurité
principales.
L’ordre des articles dans la présente norme n’est aucunement lié à leur importance. Selon les circonstances,
les mesures de sécurité, qu’elles figurent dans un article quel qu’il soit ou dans tous les articles, peuvent
s’avérer importantes: par conséquent, il convient que chaque organisation appliquant la présente norme
identifie les mesures appropriées, leur importance et leur application aux processus métier ciblés. Plus
généralement, les listes contenues dans la présente norme ne sont pas classées par ordre de priorité.
© ISO/CEI 2013 – Tous droits réservés 1
ISO/CEI 27002:2013(F)
4.2 Catégories de mesures
Chaque catégorie principale de mesures comprend:
a) un objectif de sécurité identifiant le but à atteindre,
b) une ou plusieurs mesures pouvant être appliquées en vue d’atteindre l’objectif de sécurité.
La description des mesures est structurée de la manière suivante:
Mesure
Spécifie la mesure adaptée à l’objectif de sécurité.
Préconisations de mise en œuvre
Propose des informations détaillées pour mettre en œuvre la mesure et pour atteindre l’objectif de
sécurité. Les préconisations peuvent ne pas être tout à fait adaptées ou suffisantes dans toutes les
situations et peuvent ne pas répondre aux exigences spécifiques de l’organisation en matière de sécurité.
Informations supplémentaires
Présente des compléments d’information à considérer, par exemple des éléments juridiques et des
références à d’autres normes. En l’absence de compléments d’information, cette rubrique n’apparaît pas.
5 Politiques de sécurité de l’information
5.1 Orientations de la direction en matière de sécurité de l’information
Objectif: Apporter à la sécurité de l’information une orientation et un soutien de la part de la direc-
tion, conformément aux exigences métier et aux lois et règlements en vigueur.
5.1.1 Politiques de sécurité de l’information
Mesure
Il convient de définir un ensemble de politiques en matière de sécurité de l’information qui soit approuvé
par la direction, diffusé et communiqué aux salariés et aux tiers concernés.
Préconisations de mise en œuvre
Il convient que les organisations définissent, à leur plus haut niveau, une «politique de sécurité de
l’information», qui soit approuvée par la direction et qui décrive l’approche adoptée pour gérer les
objectifs de sécurité de l’information.
Il convient que les politiques de sécurité de l’information traitent des exigences créées par:
a) la stratégie d’entreprise;
b) les réglementations, la législation et les contrats;
c) l’environnement réel et anticipé des menaces liées à la sécurité de l’information.
Il convient que cette politique de sécurité de l’information comporte des précisions concernant:
a) une définition de la sécurité de l’information, ses objectifs et ses principes pour orienter toutes les
activités relatives à la sécurité de l’information;
b) l’attribution de responsabilités générales et spécifiques en matière de management de la sécurité de
l’information à des fonctions définies;
2 © ISO/CEI 2013 – Tous droits réservés
ISO/CEI 27002:2013(F)
c) des processus de traitement des dérogations et des exceptions.
Il convient qu’à un niveau inférieur, la politique de sécurité de l’information soit étayée par des politiques
portant sur des thèmes spécifiques, qui imposent en outre la mise en œuvre de mesures de sécurité de
l’information et sont de manière générale structurées pour répondre aux besoins de certains groupes
cibles d’une organisation ou pour englober certains thèmes.
Voici des exemples de politiques à thèmes:
a) le contrôle d’accès (voir l’Article 9);
b) la classification (et le traitement) de l’information (voir 8.2);
c) la sécurité physique et environnementale (voir l’Article 11);
d) thèmes axés sur l’utilisateur final:
1) utilisation correcte des actifs (voir 8.1.3);
2) bureau propre et écran vide (voir 11.2.9);
3) transfert de l’information (voir 13.2.1);
4) appareils mobiles et télétravail (voir 6.2);
5) restrictions en matière d’installation et d’utilisation de logiciels (voir 12.6.2);
e) sauvegarde (voir 12.3);
f) transfert de l’information (voir 13.2);
g) protection contre les logiciels malveillants (voir 12.2);
h) gestion des vulnérabilités techniques (voir 12.6.1);
i) mesures de sécurité cryptographiques (voir l’Article 10);
j) sécurité des communications (voir l’Article 13);
k) protection de la vie privée et des informations personnelles identifiables (voir 18.1.4);
l) relations avec les fournisseurs (voir l’Article 15).
Il convient que ces politiques soient communiquées aux salariés et aux tiers concernés sous une
forme pertinente, accessible et compréhensible par leurs destinataires, par exemple dans le contexte
d’un «programme d’apprentissage, de formation et de sensibilisation à la sécurité de l’information»
(voir 7.2.2).
Informations supplémentaires
Le besoin en politiques internes liées à la sécurité de l’information varie en fonction des organisations.
Les politiques internes sont particulièrement utiles pour les organisations les plus grandes et les
plus complexes, dans lesquelles les personnes qui définissent et approuvent les niveaux attendus des
mesures sont isolées des personnes mettant en œuvre ces mesures, ou dans les situations où une
politique s’applique à un certain nombre de personnes ou de fonctions différentes dans l’organisation.
Les politiques de sécurité de l’information peuvent être diffusées dans un document unique «politique
de sécurité de l’information» ou dans un ensemble de documents séparés, mais interdépendants.
Si l’une quelconque des politiques de sécurité de l’information est diffusée hors de l’organisation, il
convient de veiller à ne pas divulguer d’informations confidentielles.
Certaines organisations utilisent des termes différents pour désigner ces documents de politiques, tels
que «normes», «directives» ou «règles».
© ISO/CEI 2013 – Tous droits réservés 3
ISO/CEI 27002:2013(F)
5.1.2 Revue des politiques de sécurité de l’information
Mesure
Pour garantir la constance de la pertinence, de l’adéquation et de l’efficacité des politiques liées à la
sécurité de l’information, il convient de revoir ces politiques à intervalles programmés ou en cas de
changements majeurs.
Préconisations de mise en œuvre
Il convient que chaque politique ait un propriétaire ayant accepté la responsabilité de développer,
revoir et évaluer cette politique. Il convient que la revue comporte une appréciation des possibilités
d’amélioration de la politique de l’organisation et une approche de management de la sécurité de
l’information pour répondre aux changements intervenant dans l’environnement organisationnel, aux
circonstances liées à l’activité, au contexte juridique ou à l’environnement technique.
Il convient que la revue des politiques de sécurité de l’information tienne compte des revues de direction.
Une fois révisée, il convient que la politique de sécurité soit approuvée par la direction.
6 Organisation de la sécurité de l’information
6.1 Organisation interne
Objectif: Établir un cadre de gestion pour engager, puis vérifier la mise en œuvre et le fonctionnement
de la sécurité de l’information au sein de l’organisation.
6.1.1 Fonctions et responsabilités liées à la sécurité de l’information
Mesure
Il convient de définir et d’attribuer toutes les responsabilités en matière de sécurité de l’information.
Préconisations de mise en œuvre
Il convient d’attribuer les responsabilités en matière de sécurité de l’information conformément à la
politique de sécurité de l’information (voir 5.1.1). Il convient de déterminer les responsabilités en ce qui
concerne la protection des actifs individuels et la mise en œuvre de processus de sécurité spécifiques.
Il convient de déterminer les responsabilités liées aux activités de gestion des risques en matière de
sécurité de l’information et, en particulier, celles liées à l’acceptation des risques résiduels. Si nécessaire,
il convient de compléter ces responsabilités de directives détaillées, appropriées à certains sites et
moyens de traitement de l’information. Il convient de déterminer les responsabilités locales en ce qui
concerne la protection des actifs et la mise en œuvre des processus de sécurité spécifiques.
Les personnes auxquelles ont été attribuées des responsabilités en matière de sécurité peuvent déléguer
des tâches de sécurité. Néanmoins, elles demeurent responsables et il convient qu’elles s’assurent de la
bonne exécution de toute tâche déléguée.
Il convient de préciser les domaines de responsabilité de chacun et notamment de prendre les
mesures suivantes:
a) il convient d’identifier et de déterminer les actifs et les processus de sécurité;
b) il convient d’affecter une entité responsable à chaque actif ou processus et de documenter ses
responsabilités dans le détail (voir 8.1.2);
c) il convient de définir et de documenter les différents niveaux d’autorisation;
4 © ISO/CEI 2013 – Tous droits réservés
ISO/CEI 27002:2013(F)
d) Pour être à même d’assurer les responsabilités relevant de leur domaine en matière de sécurité, il
convient que les personnes désignées soient compétentes dans ce domaine et qu’elles bénéficient de
possibilités leur permettant de se tenir au courant des évolutions;
e) Il convient d’identifier et de documenter les activités de coordination et de supervision relatives aux
questions de sécurité liées aux relations avec les fournisseurs.
Informations supplémentaires
De nombreuses organisations désignent un responsable de la sécurité de l’information pour assumer
la responsabilité d’ensemble de l’élaboration et de la mise en œuvre de la politique de sécurité de
l’information et pour corroborer l’identification des mesures de sécurité.
Cependant, la mise en place des ressources et des mesures reste bien souvent l’affaire des autres
managers. Une pratique courante consiste à nommer, pour chaque actif, un propriétaire qui devient
alors responsable de la protection quotidienne de cet actif.
6.1.2 Séparation des tâches
Mesure
Il convient de séparer les tâches et les domaines de responsabilité incompatibles pour limiter les
possibilités de modification ou de mauvais usage, non autorisé(e) ou involontaire, des actifs de
l’organisation.
Préconisations de mise en œuvre
Il convient de veiller à ce que personne ne puisse accéder à, modifier ou utiliser des actifs sans en avoir
reçu l’autorisation ou sans avoir été détecté. Il convient de séparer le déclenchement d’un événement
de son autorisation. Il convient d’envisager la possibilité de collusion lors de la conception des mesures.
Les organisations de petite taille peuvent avoir des difficultés à réaliser une séparation des tâches, mais
il convient d’appliquer ce principe dans la mesure du possible. Lorsqu’il est difficile de procéder à la
séparation des tâches, il convient d’envisager d’autres mesures comme la surveillance des activités, des
systèmes de traçabilité et la supervision de la direction.
Informations supplémentaires
La séparation des tâches est une méthode permettant de diminuer les risques de mauvais usage,
accidentel ou délibéré, des actifs d’une organisation.
6.1.3 Relations avec les autorités
Mesure
Il convient d’entretenir des relations appropriées avec les autorités compétentes.
Préconisations de mise en œuvre
Il convient que les organisations mettent en place des procédures spécifiant quand et comment il
convient de contacter les autorités compétentes (par exemple, les autorités chargées de l’application
des lois, les organismes de réglementation, les autorités de surveillance). Ces procédures définissent
également comment il convient de signaler dans les meilleurs délais les incidents liés à la sécurité de
l’information (par exemple, en cas de suspicion de violation de la loi).
Informations supplémentaires
Les organisations subissant une attaque par le biais d’Internet peuvent recourir aux autorités pour
engager des actions à l’encontre de la source de l’attaque.
Entretenir de telles relations peut constituer une exigence afin de favoriser la gestion des incidents
(voir l’Article 16) ou le processus de planification des mesures d’urgence et de continuité de l’activité
© ISO/CEI 2013 – Tous droits réservés 5
ISO/CEI 27002:2013(F)
(voir l’Article 17). Les relations avec les autorités de régulation sont également utiles pour anticiper et
préparer les changements à venir sur le plan juridique ou réglementaire, qui doivent être mis en œuvre
par l’organisation. Les relations avec les autres autorités concernent les services collectifs, les services
d’urgence, les fournisseurs d’électricité, la santé et la sécurité, comme la caserne de pompiers (pour la
continuité de l’activité), les opérateurs en télécommunication (pour le routage et la disponibilité) et les
sociétés de distribution d’eau (pour le refroidissement du matériel).
6.1.4 Relations avec des groupes de travail spécialisés
Mesure
Il convient d’entretenir des relations appropriées avec des groupes d’intérêt, des forums spécialisés
dans la sécurité et des associations professionnelles.
Préconisations de mise en œuvre
Il convient d’envisager une inscription à des groupes d’intérêt ou à des forums spécialisés aux fins suivantes:
a) mieux connaître les bonnes pratiques et se tenir informé de l’évolution des savoirs relatifs à la sécurité;
b) s’assurer que la connaissance de l’environnement de la sécurité de l’information est à jour et exhaustive;
c) recevoir rapidement des alertes, des conseils et des correctifs logiciels portant sur les attaques et
les vulnérabilités;
d) avoir accès à des conseils de spécialistes sur la sécurité de l’information;
e) partager et échanger des informations sur les nouvelles technologies, les produits, les menaces ou
les vulnérabilités;
f) mettre en place des relais d’information appropriés lors du traitement d’incidents liés à la sécurité
de l’information (voir 16).
Informations supplémentaires
Des accords de partage de l’information peuvent être établis en vue d’améliorer la coopération et la
coordination dans le domaine de la sécurité. Il convient que de tels accords identifient les exigences en
matière de protection des informations confidentielles.
6.1.5 La sécurité de l’information dans la gestion de projet
Mesure
Il convient de traiter la sécurité de l’information dans la gestion de projet, quel que soit le type de
projet concerné.
Préconisations de mise en œuvre
Il convient d’intégrer la sécurité de l’information dans la ou les méthodes de gestion de projet de
l’organisation pour veiller à ce que les risques de sécurité de l’information soient identifiés et traités
dans le cadre du projet. Cette préconisation s’applique de manière générale à tout projet quel qu’il soit,
indépendamment de sa nature, par exemple un projet lié à un processus clé de l’activité, aux technologies
de l’information, à la gestion des installations et autres processus. Il convient que les méthodes de gestion
de projet en vigueur imposent que:
a) les objectifs en matière de sécurité de l’information soient intégrés aux objectifs du projet;
b) une appréciation du risque de sécurité de l’information soit effectuée au commencement du projet
pour identifier les mesures nécessaires;
c) la sécurité de l’information soit intégrée à toutes les phases de la méthodologie de projet appliquée.
6 © ISO/CEI 2013 – Tous droits réservés
ISO/CEI 27002:2013(F)
Pour tous les projets, il convient de traiter et de revoir régulièrement les incidences sur la sécurité de
l’information. Il convient de déterminer et d’attribuer les responsabilités en matière de sécurité de
l’information à des fonctions spécifiques définies dans les méthodes de gestion de projet.
6.2 Appareils mobiles et télétravail
Objectif: Assurer la sécurité du télétravail et de l’utilisation d’appareils mobiles.
6.2.1 Politique en matière d’appareils mobiles
Mesure
Il convient d’adopter une politique et des mesures de sécurité complémentaires pour gérer les risques
découlant de l’utilisation des appareils mobiles.
Préconisations de mise en œuvre
Lors de l’utilisation d’appareils mobiles, il convient de veiller particulièrement à ce que les informations
liées à l’activité de l’organisation ne soient pas compromises. Il convient que la politique en matière
d’appareils mobiles tienne compte des risques liés au fait de travailler avec des appareils mobiles dans
des environnements non protégés.
Il convient que la politique en matière d’appareils mobiles envisage:
a) l’enregistrement des appareils mobiles;
b) les exigences liées à la protection physique;
c) les restrictions liées à l’installation de logiciels;
d) les exigences liées aux versions logicielles des appareils mobiles et à l’application de correctifs;
e) les restrictions liées aux connexions à des services d’information;
f) les contrôles d’accès;
g) les techniques cryptographiques;
h) la protection contre les logiciels malveillants;
i) la désactivation, l’effacement des données ou le verrouillage à distance;
j) les sauvegardes;
k) l’utilisation des services web et des applications web.
Il convient d’être vigilant lors de l’utilisation d’appareils mobiles dans des lieux publics, des salles de
réunions et autres zones non protégées. Il convient de mettre en place des mesures de protection visant à
empêcher les accès non autorisés ou la divulgation d’informations stockées et traitées par ces appareils,
par exemple en utilisant des techniques cryptographiques (voir l’Article 10) et en imposant l’utilisation
d’informations d’authentification secrètes (voir 9.2.3).
Il convient également que les appareils mobiles soient physiquement protégés contre le vol, en
particulier lorsqu’ils sont laissés, par exemple, dans un véhicule privé ou tout autre moyen de transport,
une chambre d’hôtel, un centre de congrès ou une salle de réunion. Il convient d’établir une procédure
spécifique tenant compte des exigences juridiques, des exigences liées aux assurances et des exigences
de sécurité de l’organisation, en cas de vol ou de perte d’appareils mobiles. Il convient de ne pas laisser
sans surveillance les appareils dans lesquels sont stockées des informations importantes, sensibles
ou critiques liées à l’activité de l’organisation et, si possible, de les mettre
...
SLOVENSKI SIST ISO/IEC 27002
STANDARD november 2013
Informacijska tehnologija – Varnostne tehnike – Pravila obnašanja pri
kontrolah informacijske varnosti
Information technology – Security techniques – Code of practice for information
security controls
Technologies de l'information – Techniques de sécurité – Code de bonne
pratique pour le management de la sécurité de l'information
Referenčna oznaka
ICS 35.040 SIST ISO/IEC 27002:2013 (sl)
Nadaljevanje na straneh od 2 do 84
© 2014-02. Slovenski inštitut za standardizacijo. Razmnoževanje celote ali delov tega standarda ni dovoljeno.
SIST ISO/IEC 27002 : 2013
NACIONALNI UVOD
Standard SIST ISO/IEC 27002 (sl), Informacijska tehnologija – Varnostne tehnike – Pravila obnašanja
pri upravljanju informacijske varnosti, 2013, ima status slovenskega standarda in je istoveten
mednarodnemu standardu ISO/IEC 27002 (en), Information technology – Security techniques – Code
of practice for information security management, druga izdaja, 2013-10-01.
NACIONALNI PREDGOVOR
Mednarodni standard ISO/IEC 27002:2013 je pripravil pododbor združenega tehničnega odbora
Mednarodne organizacije za standardizacijo in Mednarodne elektrotehniške komisije ISO/IEC JTC
1/SC 27 Varnostne tehnike v informacijski tehnologiji.
Slovenski standard SIST ISO/IEC 27002:2013 je prevod mednarodnega standarda ISO/IEC
27002:2013. V primeru spora glede besedila slovenskega prevoda je odločilen izvirni mednarodni
standard v angleškem jeziku. Slovenski standard SIST ISO/IEC 27002:2013 je pripravil tehnični odbor
SIST/TC ITC Informacijska tehnologija.
Odločitev za izdajo tega standarda je dne 25. oktobra 2013 sprejel SIST/TC ITC Informacijska
tehnologija.
ZVEZA Z NACIONALNIMI STANDARDI
S prevzemom tega evropskega standarda veljajo za omejeni namen referenčnih standardov vsi
standardi, navedeni v izvirniku, razen standardov, ki so že sprejeti v nacionalno standardizacijo:
SIST ISO/IEC 27000 Informacijska tehnologija – Varnostne tehnike – Sistemi upravljanja
informacijske varnosti – Pregled in izrazoslovje
OSNOVA ZA IZDAJO STANDARDA
– privzem standarda ISO/IEC 27002:2013
PREDHODNA IZDAJA
– SIST ISO/IEC 27002:2008
OPOMBI
– Povsod, kjer se v besedilu standarda uporablja izraz “mednarodni standard”, v SIST ISO/IEC
27002:2013 to pomeni “slovenski standard”.
– Nacionalni uvod in nacionalni predgovor nista sestavni del standarda.
SIST ISO/IEC 27002 : 2013
VSEBINA Stran
Predgovor .7
0 Uvod .8
0.1 Ozadje in kontekst.8
0.2 Zahteve informacijske varnosti.8
0.3 Izbiranje kontrol .9
0.4 Razvijanje lastnih smernic.9
0.5 Razmisleki o življenjskem ciklu .9
0.6 Sorodni standardi .9
1 Področje uporabe .10
2 Zveze s standardi .10
3 Izrazi in definicije .10
4 Struktura tega standarda.10
4.1 Točke.10
4.2 Kategorije kontrol.10
5 Informacijske varnostne politike .11
5.1 Usmeritev vodstva za informacijsko varnost.11
5.1.1 Politike za informacijsko varnost .11
5.1.2 Pregled politik za informacijsko varnost.12
6 Organiziranje informacijske varnosti .12
6.1 Notranja organizacija.12
6.1.1 Vloge in odgovornosti na področju informacijske varnosti.12
6.1.2 Razmejitev dolžnosti .13
6.1.3 Stik s pristojnimi organi .13
6.1.4 Stik s specifičnimi interesnimi skupinami .14
6.1.5 Informacijska varnost v upravljanju projektov .14
6.2 Mobilne naprave in delo na daljavo.15
6.2.1 Politika na področju mobilnih naprav .15
6.2.2 Delo na daljavo.16
7 Varnost človeških virov.17
7.1 Pred zaposlovanjem.17
7.1.1 Preverjanje .17
7.1.2 Določila in pogoji za zaposlitev .18
7.2 Med zaposlitvijo.19
7.2.1 Odgovornosti vodstva.19
7.2.2 Ozaveščenost, izobraževanje in usposabljanje o informacijski varnosti .19
7.2.3 Disciplinski proces.20
7.3 Prekinitev ali sprememba zaposlitve.21
7.3.1 Prekinitev ali sprememba zaposlitveniih odgovornosti .21
8 Upravljanje dobrin.21
8.1 Odgovornost za dobrine.21
8.1.1 Popis dobrin.21
8.1.2 Lastništvo nad dobrinami .22
8.1.3 Sprejemljiva uporaba dobrin.22
SIST ISO/IEC 27002 : 2013
8.1.4 Vračilo dobrin.23
8.2 Razvrstitev informacij .23
8.2.1 Razvrstitev informacij .23
8.2.2 Označevanje informacij.24
8.2.3 Ravnanje z dobrinami.24
8.3 Ravnanje z nosilci podatkov/informacij .25
8.3.1 Upravljanje izmenljivih nosilcev podatkov/informacij .25
8.3.2 Odstranjevanje nosilcev podatkov/informacij.25
8.3.3 Prenos fizičnih nosilcev podatkov/informacij.26
9 Nadzor dostopa .27
9.1 Nadzor dostopa .27
9.1.1 Politika nadzora dostopa.27
9.1.2 Dostop do omrežij in omrežnih storitev.28
9.2 Upravljanje uporabniškega dostopa.28
9.2.1 Registracija in izbris registracije uporabnika.28
9.2.2 Zagotavljanje dostopa uporabnikom .29
9.2.3 Upravljanje posebnih pravic dostopa .29
9.2.4 Upravljanje tajnih informacij uporabnikov za preverjanje verodostojnosti .30
9.2.5 Pregled uporabniških pravic dostopa.31
9.2.6 Preklic ali prilagoditev pravic dostopa .31
9.3 Odgovornosti uporabnikov .32
9.3.1 Uporaba tajnih informacij za preverjanje verodostojnosti .32
9.4 Nadzor dostopa do sistemov in aplikacij .33
9.4.1 Omejitev dostopa do informacij.33
9.4.2 Varni postopki prijave .33
9.4.3 Sistem upravljanja gesel .34
9.4.4 Uporaba posebnih pomožnih programov.34
9.4.5 Nadzor dostopa do programske izvorne kode .35
10 Kriptografija .36
10.1 Kriptografske kontrole .36
10.1.1 Politika uporabe kriptografskih kontrol .36
10.1.2 Upravljanje ključev .37
11 Fizična in okoljska varnost .38
11.1 Varovana območja .38
11.1.1 Varovanje fizičnih meja območja.38
11.1.2 Kontrole fizičnega vstopa .39
11.1.3 Varovanje pisarn, sob in naprav.39
11.1.4 Zaščita pred zunanjimi in okoljskimi grožnjami .40
11.1.5 Delo na varovanih območjih.40
11.1.6 Dostavne in nakladalne površine .40
11.2 Oprema.40
11.2.1 Namestitev in zaščita opreme .41
11.2.2 Podporna oskrba .41
11.2.3 Varnost ožičenja.42
11.2.4 Vzdrževanje opreme .42
SIST ISO/IEC 27002 : 2013
11.2.5 Odstranitev dobrin .42
11.2.6 Varnost opreme in dobrin zunaj prostorov organizacije.43
11.2.7 Varna odstranitev ali ponovna uporaba opreme .43
11.2.8 Nenadzorovana uporabniška oprema.44
11.2.9 Politika čiste mize in praznega zaslona .44
12 Varnost operacij.45
12.1 Operativni postopki in odgovornosti .45
12.1.1 Dokumentirani postopki delovanja .45
12.1.2 Upravljanje sprememb .46
12.1.3 Upravljanje zmogljivosti.46
12.1.4 Ločevanje razvojnih, testnih in obratovalnih naprav .47
12.2 Zaščita pred zlonamerno programsko opremo .48
12.2.1 Kontrole proti zlonamerni programski opremi .48
12.3 Varnostno kopiranje .49
12.3.1 Varnostno kopiranje informacij.49
12.4 Beleženje in spremljanje .50
12.4.1 Beleženje dogodkov.50
12.4.2 Zaščita zabeleženih informacij .51
12.4.3 Beleženje aktivnosti administratorjev in operaterjev.51
12.4.4 Uskladitev ur.51
12.5 Nadzor operativne programske opreme.52
12.5.1 Namestitev programske opreme na operativne sisteme.52
12.6 Upravljanje tehničnih ranljivosti.53
12.6.1 Upravljanje tehničnih ranljivosti.53
12.6.2 Omejitve pri namestitvi programske opreme.54
12.7 Upoštevanje presoj informacijskih sistemov .54
12.7.1 Kontrole presoje informacijskih sistemov.55
13 Varnost komunikacije .55
13.1 Upravljanje varovanja omrežij .55
13.1.1 Omrežne kontrole.55
13.1.2 Varovanje omrežnih storitev.56
13.3.4 Ločevanje v omrežjih.56
13.2 Prenos informacij.57
13.2.1 Politike in postopki prenosa informacij.57
13.2.2 Dogovori o prenosu informacij .58
13.2.3 Elektronsko sporočanje.58
13.2.4 Dogovori o zaupnosti ali nerazkrivanju .59
14 Pridobivanje, razvoj in vzdrževanje sistemov.60
14.1 Varnostne zahteve informacijskih sistemov .60
14.1.1 Analiza in specifikacije informacijskih varnostnih zahtev.60
14.1.2 Varovanje aplikacijskih storitev v javnih omrežjih .61
14.1.3 Zaščita transakcij aplikacijskih storitev.62
14.2 Varnost v procesih razvoja in podpore.62
14.2.1 Varna razvojna politika.62
14.2.2 Postopki nadzora sprememb sistemov .63
SIST ISO/IEC 27002 : 2013
14.2.3 Tehnični pregled aplikacij po spremembah operacijskih sistemov .64
14.2.4 Omejitve pri spremembah programskih paketov .64
14.2.5 Načela varnega sistemskega inženiringa .65
14.2.6 Varno razvojno okolje.65
14.2.7 Zunanje izvajanje razvoja .66
14.2.8 Testiranje sistemske varnosti.66
14.2.9 Testiranje prevzema sistema .67
14.3 Testni podatki .67
14.3.1 Zaščita testnih podatkov .67
15 Odnosi z dobavitelji .67
15.1 Informacijska varnost v odnosih z dobavitelji.67
15.1.1 Informacijska varnostna politika za odnose z dobavitelji .68
15.1.2 Obravnavanje varnosti v dogovorih z dobavitelji.69
15.1.3 Dobavna veriga informacijske in komunikacijske tehnologije .70
15.2 Upravljanje izvajanja storitev dobavitelja .70
15.2.1 Spremljanje in pregledovanje storitev dobaviteljev .71
15.2.2 Upravljanje sprememb storitev dobaviteljev.71
16 Upravljanje informacijskih varnostnih incidentov .72
16.1 Upravljanje informacijskih varnostnih incidentov in izboljšave.72
16.1.1 Odgovornosti in postopki.72
16.1.2 Poročanje o informacijskih varnostnih dogodkih.73
16.1.3 Poročanje o informacijskih varnostnih slabostih .74
16.1.4 Ocena informacijskih varnostnih dogodkov in odločitev o njih.74
16.1.5 Odgovor na informacijske varnostne incidente .74
16.1.6 Učenje iz informacijskih varnostnih incidentov.75
16.1.7 Zbiranje dokazov .75
17 Vidiki informacijske varnosti pri upravljanju neprekinjenega poslovanja .76
17.1 Neprekinjena informacijska varnost .76
17.1.1 Načrtovanje neprekinjene informacijske varnosti.76
17.1.2 Izvajanje neprekinjene informacijske varnosti.77
17.1.3 Preverjanje, pregledovanje in vrednotenje neprekinjene informacijske varnosti.77
17.2 Zadostno število .78
17.2.1 Razpoložljivost naprav za obdelavo informacij .78
18 Skladnost.78
18.1 Skladnost z zakonodajnimi in pogodbenimi zahtevami .78
18.1.1 Prepoznavanje veljavnih zakonskih in pogodbenih zahtev .78
18.1.2 Pravice intelektualne lastnine.79
18.1.3 Zaščita zapisov.80
18.1.4 Zasebnost in zaščita osebno določljivih podatkov .80
18.1.5 Uporaba kriptografskih kontrol .81
18.2 Pregledi informacijske varnosti .81
18.2.1 Neodvisni pregled informacijske varnosti.81
18.2.2 Skladnost z varnostnimi politikami in standardi .82
18.2.3 Pregled tehnične skladnosti .82
Literatura .84
SIST ISO/IEC 27002 : 2013
Predgovor
ISO (Mednarodna organizacija za standardizacijo) in IEC (Mednarodna elektrotehniška komisija)
tvorita specializiran sistem za svetovno standardizacijo. Nacionalni organi, ki so člani ISO ali IEC,
sodelujejo pri pripravi mednarodnih standardov prek tehničnih odborov, ki jih za obravnavanje
določenih strokovnih področij ustanovi ustrezna organizacija. Tehnični odbori ISO in IEC sodelujejo na
področjih skupnega interesa. Pri delu sodelujejo tudi druge mednarodne, vladne in nevladne
organizacije, povezane z ISO in IEC. Na področju informacijske tehnologije sta ISO in IEC vzpostavila
združeni tehnični odbor ISO/IEC JTC 1.
Mednarodni standardi so pripravljeni v skladu s pravili iz 2. dela Direktiv ISO/IEC.
ISO/IEC 27002 je pripravil združeni tehnični odbor JTC ISO/IEC 1 Informacijska tehnologija, pododbor
SC 27 Varnostne tehnike IT.
Opozoriti je treba na možnost, da so lahko nekateri elementi tega dokumenta predmet patentnih
pravic. ISO ne prevzema odgovornosti za identifikacijo nekaterih ali vseh takih patentnih pravic.
Druga izdaja preklicuje in nadomešča prvo izdajo (ISO/IEC 27002:2005), ki je tehnično in strukturno
revidirana.
SIST ISO/IEC 27002 : 2013
0 Uvod
0.1 Ozadje in kontekst
Ta mednarodni standard je zasnovan, da bi ga organizacije uporabljale kot referenco pri izbiri kontrol
znotraj procesa izvajanja sistema upravljanja informacijske varnosti (ISMS) na podlagi standarda
[10]
ISO/IEC 27001 ali kot dokument z napotki za organizacije, ki izvajajo splošno sprejete kontrole
informacijske varnosti. Ta standard je namenjen tudi za uporabo pri izdelavi smernic za upravljanje
informacijske varnosti znotraj panog in organizacij, pri čemer upošteva posebne značilnosti njihovega
okolja informacijskih varnostnih tveganj.
Organizacije vseh vrst in velikosti (vključno z javnim in zasebnim ter pridobitnim in nepridobitnim
sektorjem) zbirajo, obdelujejo, shranjujejo in prenašajo informacije v mnogih oblikah, na primer
elektronsko, fizično in ustno (npr. pogovori in predstavitve).
Vrednost informacij presega zapisane besede, številke in slike: znanje, koncepti, ideje in blagovne
znamke so primeri neotipljivih oblik informacij. V medsebojno povezanem svetu so informacije ter
povezani procesi, sistemi, omrežja in osebje, vključeno v njihovo delovanje, upravljanje in zaščito,
dobrine, ki so kot druge pomembne poslovne dobrine dragocene za poslovanje organizacij in si kot
take zaslužijo ali zahtevajo zaščito pred različnimi nevarnostmi.
Dobrine so predmet namernih in naključnih groženj, ranljivosti pa so sestavni del povezanih procesov,
sistemov, omrežij in ljudi. Spremembe poslovnih procesov in sistemov ali druge zunanje spremembe
(npr. spremembe zakonov in predpisov) lahko povzročijo nova informacijska varnostna tveganja.
Zaradi velikega števila načinov, na katere lahko grožnje izkoristijo ranljivosti in škodijo organizacijam,
so informacijska varnostna tveganja vedno prisotna. Z zaščito organizacije pred grožnjami in
ranljivostmi uspešna informacijska varnost zmanjša ta tveganja in nato njihove učinke na dobrine
organizacije.
Informacijska varnost se doseže z izvajanjem ustreznih nizov kontrol, vključno s politikami, procesi,
postopki, organizacijskimi strukturami ter funkcijami programske in strojne opreme. Te kontrole je
treba vzpostaviti, izvajati, spremljati, pregledovati in izboljševati, kadar je to potrebno, da se zagotovi,
da so izpolnjeni posebni varnostni in poslovni cilji organizacije. Sistem upravljanja informacijske
[10]
varnosti, kot je naveden v standardu SO/IEC 27001 , omogoča celovit in koordiniran pogled na
informacijska varnostna tveganja organizacije, da lahko izvaja celovit niz kontrol informacijske varnosti
v okviru koherentnega sistema upravljanja.
[10]
Mnogi informacijski sistemi niso bili zasnovani kot varni sistemi v smislu standarda ISO/IEC 27001
in tega standarda. Varovanje, ki ga je mogoče doseči s tehničnimi sredstvi, je omejeno ter naj bo
podprto z ustreznim upravljanjem in postopki. Prepoznavanje, katere kontrole naj bodo nameščene,
zahteva skrbno načrtovanje in osredotočenost na podrobnosti. Za uspešen sistem upravljanja
informacijske varnosti je potrebno sodelovanje vseh zaposlenih v organizaciji. Prav tako je lahko
potrebna udeležba delničarjev, dobaviteljev ali drugih zunanjih strank. Potrebni pa so lahko tudi
strokovni nasveti zunanjih strank.
V bolj splošnem pomenu uspešna informacijska varnost zagotavlja vodstvu in drugim deležnikom, da
so dobrine organizacije primerno varne in zaščitene pred škodo, zato omogoča boljše poslovanje.
0.2 Zahteve informacijske varnosti
Bistveno je, da organizacija prepozna svoje varnostne zahteve. Glavni viri varnostnih zahtev so trije:
a) ocenjevanje tveganj organizacije ob upoštevanju celovite poslovne strategije in ciljev
organizacije. Z oceno tveganj se prepoznajo grožnje dobrinam, ovrednotita se ranljivost in
verjetnost pojava ter oceni se potencialni vpliv;
b) pravne, zakonske, regulativne in pogodbene zahteve, ki jih morajo izpolniti organizacija, njeni
poslovni partnerji, pogodbeniki in ponudniki storitev, ter njihovo družbeno-kulturno okolje;
SIST ISO/IEC 27002 : 2013
c) niz načel, ciljev in poslovnih zahtev za upravljanje, obdelavo, shranjevanje, prenos in
shranjevanje informacij, ki ga je organizacija razvila za podporo svojemu delovanju.
Viri, ki se uporabljajo za izvajanje kontrol, morajo biti zaščiteni pred poslovno škodo, do katere utegne
priti zaradi varnostnih tveganj zaradi odsotnosti takih kontrol. Rezultati ocenjevanja tveganj bodo
pomagali voditi in določiti ustrezne ukrepe vodstva in prednostne naloge za upravljanje informacijskih
varnostnih tveganj ter za izvajanje kontrol, izbranih za varovanje pred temi tveganji.
[11]
Standard ISO/IEC 27005 podaja navodila za upravljanje informacijskih varnostnih tveganj, vključno
z napotkom za ocenjevanje, obravnavanje in sprejetje tveganj, obveščanje o tveganjih ter za
spremljanje in pregled tveganj.
0.3 Izbiranje kontrol
Kontrole se lahko izberejo iz tega standarda ali drugih nizov kontrol ali pa se lahko zasnujejo nove
kontrole za izpolnitev ustreznih posebnih potreb.
Izbor kontrol je odvisen od organizacijskih odločitev, ki temeljijo na kriterijih za sprejetje tveganj,
možnostih obravnavanja tveganj ter na splošnem pristopu k upravljanju tveganj, ki ga uporablja
organizacija, ter naj ustreza vsem ustreznim nacionalnim in mednarodnim zakonodajam in predpisom.
Izbira kontrol je odvisna tudi od načina, kako kontrole vzajemno delujejo, kar omogoča globoko
zaščito.
Nekatere kontrole v tem standardu je mogoče obravnavati kot vodilna načela za upravljanje
informacijske varnosti in ustrezajo večini organizacij. Te kontrole so podrobneje razložene spodaj
skupaj z napotki za izvajanje. Več informacij o izbiranju kontrol in drugih možnostih obravnavanja
[11]
tveganj je mogoče najti v standardu ISO/IEC 27005.
0.4 Razvijanje lastnih smernic
Ta mednarodni standard je mogoče upoštevati kot izhodišče za razvoj posebnih smernic organizacije.
Vse kontrole in smernice iz teh pravil obnašanja morda niso primerne. Poleg tega so lahko potrebne
dodatne kontrole in smernice, ki niso vključene v ta standard. Ko bodo razviti dokumenti z dodatnimi
kontrolami ali smernicami, bo morda koristno vključiti sklice na točke v tem standardu, kjer je to
primerno, kar bo olajšalo preverjanje skladnosti presojevalcem in poslovnim partnerjem.
0.5 Razmisleki o življenjskem ciklu
Informacije imajo naravni življenjski cikel: od ustvarjanja in nastanka prek shranjevanja, obdelave in
prenosa do morebitnega uničenja ali propada. Vrednost dobrin in tveganj zanje se lahko med
življenjskim ciklom spreminjajo (npr. nepooblaščeno razkritje ali kraja finančnih računov podjetja je
manj pomembna, potem ko so bili že uradno objavljeni), vendar informacijska varnost ostaja relativno
pomembna v vseh obdobjih.
Informacijski sistemi imajo življenjske cikle, znotraj katerih so ustvarjeni, določeni, načrtovani, razviti,
testirani, uvedeni, uporabljeni, vzdrževani in morebiti umaknjeni oziroma zavrženi. Informacijska
varnost bi morala biti upoštevana v vsakem obdobju. Razvoj novih in spremembe obstoječih sistemov
organizacijam omogočajo, da posodobijo in izboljšajo varnostne kontrole, pri tem pa upoštevajo
dejanske incidente ter trenutna in predvidena informacijska varnostna tveganja.
0.6 Sorodni standardi
Čeprav ta standard podaja smernice za širok razpon kontrol informacijske varnosti, ki se navadno
uporabljajo v številnih različnih organizacijah, drugi standardi skupine ISO/IEC 27000 podajajo
dodatne zahteve ali nasvete o drugih vidikih celotnega procesa upravljanja informacijske varnosti.
Splošni uvod v sisteme upravljanja informacijske varnosti in skupino standardov je podan v standardu
ISO/IEC 27000. Standard ISO/IEC 27000 vsebuje glosar, v katerem je uradno definirana večina
izrazov, ki se uporabljajo v skupini standardov ISO/IEC 27000. Ta standard opisuje tudi področje
uporabe in cilje vsakega standarda v skupini.
SIST ISO/IEC 27002 : 2013
Informacijska tehnologija – Varnostne tehnike – Pravila obnašanja pri
kontrolah informacijske varnosti
1 Področje uporabe
Ta mednarodni standard podaja smernice za standarde informacijske varnosti organizacij in načine
uporabe upravljanja informacijske varnosti, kar vključuje izbiro, izvajanje in upravljanje kontrol, pri
čemer upošteva informacijska varnostna tveganja okolja(-ij) organizacije.
Ta mednarodni standard je zasnovan, da ga uporabijo organizacije, ki želijo:
a) izbrati kontrole znotraj procesa izvajanja sistema upravljanja informacijske varnosti na podlagi
[10]
ISO/IEC 27001,
b) izvajati splošno sprejete kontrole informacijske varnosti,
c) razvijati lastne smernice za upravljanje informacijske varnosti.
2 Zveze s standardi
Pri uporabi tega standarda so, delno ali v celoti, nujno potrebni spodaj navedeni referenčni dokumenti.
Pri datiranih sklicevanjih se uporablja le navedena izdaja. Pri nedatiranih sklicevanjih se uporablja
zadnja izdaja publikacije (vključno z dopolnili).
ISO/IEC 27000 Informacijska tehnologija – Varnostne tehnike – Sistemi upravljanja
informacijske varnosti – Pregled in izrazoslovje
3 Izrazi in definicije
V tem dokumentu so uporabljeni izrazi in definicije, podani v ISO/IEC 27000.
4 Struktura tega standarda
Ta standard vsebuje 14 točk o varnostnih kontrolah, ki skupaj tvorijo 35 glavnih varnostnih kategorij in
114 kontrol.
4.1 Točke
Vsaka točka, ki definira varnostne kontrole, vsebuje eno ali več glavnih varnostnih kategorij.
Vrstni red točk v tem standardu ne nakazuje njihove pomembnosti. Varnostne kontrole iz vseh ali
katere koli točke so lahko pomembne, odvisno od okoliščin, zato naj vsaka organizacija, ki uporablja
ta standard, določi njihovo pomembnost in uporabo v posameznih poslovnih procesih. Prav tako
seznami v tem standardu niso zapisani v prednostnem vrstnem redu.
4.2 Kategorije kontrol
Vsaka glavna kategorija varnostnih kontrol vsebuje:
a) cilj kontrole, ki navaja, kaj je treba doseči,
b) eno ali več kontrol, ki jih je mogoče uporabiti za doseganje cilja kontrole.
Opisi kontrol so strukturirani na naslednji način:
Kontrola
Določa specifične kontrolne izjave za izpolnitev cilja kontrole.
Napotki za izvajanje
Zagotavljajo podrobnejše informacije v podporo izvedbi kontrole in doseganju njenega cilja. Napotki
morda niso popolnoma primerni ali zadostni v vseh situacijah in morda ne izpolnijo posebnih zahtev
kontrole organizacije.
SIST ISO/IEC 27002 : 2013
Druge informacije
Zagotovijo nadaljnje informacije, ki jih je morda treba upoštevati, na primer pravne vidike in
sklicevanje na druge standarde. Če druge informacije niso podane, tega dela besedila ni.
5 Informacijske varnostne politike
5.1 Usmeritev vodstva za informacijsko varnost
Cilj: Zagotoviti usmeritve vodstva in njegovo podporo informacijski varnosti v skladu s poslovnimi
zahtevami ter ustreznimi zakoni in predpisi.
5.1.1 Politike za informacijsko varnost
Kontrola
Opredeli naj se sklop politik za informacijsko varnost, ki jih odobri vodstvo, ter se objavi in sporoči
zaposlenim in ustreznim zunanjim strankam.
Napotki za izvajanje
Organizacije naj na najvišji ravni opredelijo "informacijsko varnostno politiko", ki jo odobri vodstvo in ki
določi pristop organizacije k upravljanju njenih ciljev informacijske varnosti.
Informacijske varnostne politike naj obravnavajo zahteve, ki jih ustvarijo:
a) poslovna strategija,
b) predpisi, zakonodaja in pogodbe,
c) trenutno in predvideno okolje groženj informacijski varnosti.
Informacijska varnostna politika naj vsebuje izjave o:
a) definiciji informacijske varnosti ter ciljih in načelih za vodenje vseh aktivnosti, povezanih z
informacijsko varnostjo,
b) dodeljevanju splošnih in posebnih odgovornosti za upravljanje informacijske varnosti določenim
vlogam,
c) procesih za ravnanje ob odstopanjih in izjemah.
Na nižji ravni naj informacijsko varnostno politiko podpirajo temi ustrezne politike, ki podelijo nadaljnja
pooblastila za izvajanje kontrol informacijske varnosti in so navadno strukturirane za obravnavo potreb
določenih ciljnih skupin v organizaciji ali da obravnavajo določene teme.
Primeri takih tem politike so:
a) nadzor dostopa (glej točko 9);
b) razvrstitev (in obravnavanje) informacij (glej 8.2);
c) fizična in okoljska varnost (glej točko 11);
d) teme, usmerjene na končnega uporabnika, kot so:
1) sprejemljiva uporaba dobrin (glej 8.1.3),
2) čista miza in prazen zaslon (glej 11.2.9),
3) prenos informacij (glej 13.2.1),
4) mobilne naprave in delo na daljavo (glej 6.2),
5) omejitve namestitve in uporabe programske opreme (glej 12.6.2);
e) varnostno kopiranje (glej 12.3);
SIST ISO/IEC 27002 : 2013
f) prenos informacij (glej 13.2);
g) zaščita pred zlonamerno programsko opremo (glej 12.2);
h) upravljanje tehničnih ranljivosti (glej 12.6.1);
i) kriptografske kontrole (glej točko 10);
j) komunikacijska varnost (glej točko 13);
k) zasebnost in zaščita osebno določljivih podatkov (glej 18.1.4);
l) odnosi z dobavitelji (glej točko 15).
S temi politikami naj bodo seznanjeni zaposleni in ustrezne zunanje stranke na način, ki bo
predvidenemu bralcu ustrezen, dostopen in razumljiv, npr. v kontekstu "spoznavanja informacijske
varnosti, izobraževanja in usposabljanja" (glej 7.2.2).
Druge informacije
Potreba po notranjih politikah za informacijsko varnost se v različnih delih organizacije razlikuje.
Notranje politike so posebej uporabne v večjih in bolj zapletenih organizacijah, kjer so tisti, ki določajo
in potrjujejo pričakovane ravni nadzora, ločeni od tistih, ki nadzor izvajajo, ali v primerih, ko politika
velja za številne različne ljudi ali funkcije v organizaciji. Informacijske varnostne politike je mogoče
izdati v enem dokumentu "informacijske varnostne politike" ali v naboru posameznih, a med seboj
povezanih dokumentov.
Če se katera koli od informacijskih varnostnih politik razširja zunaj organizacije, naj se pazi, da se ne
razkrijejo zaupne informacije.
Nekatere organizacije uporabljajo druge izraze za te dokumente, kot so "standardi", "direktive" ali
"pravila".
5.1.2 Pregled politik za informacijsko varnost
Kontrola
Politike za informacijsko varnost naj se pregledujejo v načrtovanih intervalih ali če se pojavijo
pomembne spremembe, da se zagotovijo njihova nenehna ustreznost, zadostnost in uspešnost.
Napotki za izvajanje
Vsaka politika naj ima lastnika, ki mu je vodstvo določilo odgovornost za razvoj, pregled in vrednotenje
politik. Pregled naj vključuje ocenjevanje možnosti za izboljšanje politik organizacije in pristop k
upravljanju informacijske varnosti kot odgovor na spremembe v organizacijskem okolju, poslovnih
okoliščinah, pravnih pogojih ali tehničnem okolju.
Pregled politik za informacijsko varnost naj upošteva rezultate vodstvenih pregledov.
Za revidirane politike naj se pridobi odobritev vodstva.
6 Organiziranje informacijske varnosti
6.1 Notranja organizacija
Cilj: Vzpostaviti okvir upravljanja za začetek in kontrolo izvajanja ter delovanja informacijske varnosti
v organizaciji.
6.1.1 Vloge in odgovornosti na področju informacijske varnosti
Kontrola
Določijo in dodelijo naj se vse odgovornosti na področju informacijske varnosti.
SIST ISO/IEC 27002 : 2013
Napotki za izvajanje
Odgovornosti za informacijsko varnost naj se dodelijo v skladu z informacijskimi varnostnimi politikami
(glej 5.1.1).
...















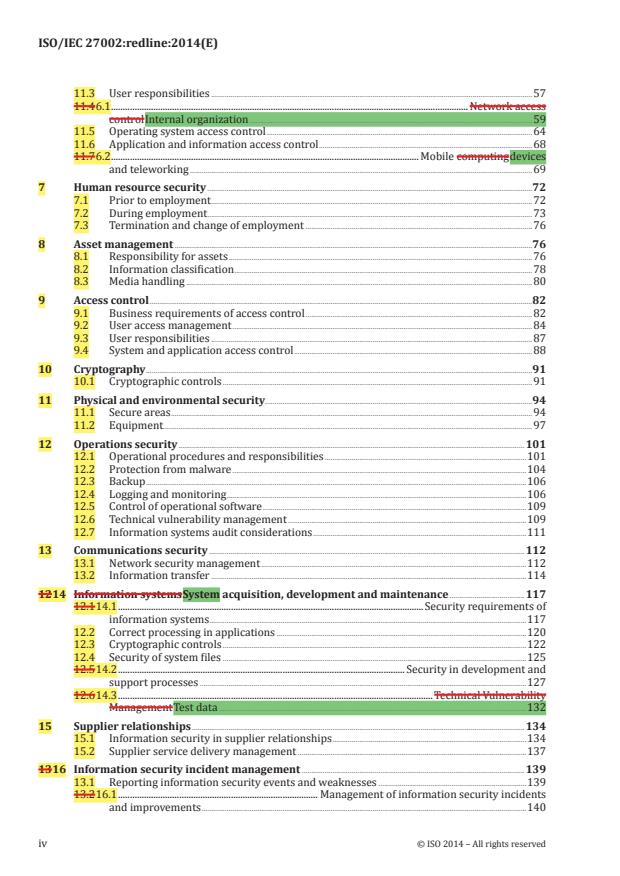












Questions, Comments and Discussion
Ask us and Technical Secretary will try to provide an answer. You can facilitate discussion about the standard in here.
Loading comments...